Access control
[2] General security policies require designing or selecting appropriate security controls to satisfy an organization's risk appetite - access policies similarly require the organization to design or select access controls.
Geographical access control may be enforced by personnel (e.g. border guard, bouncer, ticket checker), or with a device such as a turnstile.
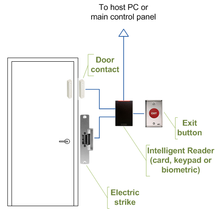
[3] The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons.
[4] Electronic access control (EAC) uses computers to solve the limitations of mechanical locks and keys.
A wide range of credentials can be used to replace mechanical keys, allowing for complete authentication, authorization, and accounting.
Typically, credentials can be something a person knows (such as a number or PIN), something they have (such as an access badge), something they are (such as a biometric feature), something they do (measurable behavioural patterns), or some combination of these items.
The built-in biometric technologies found on newer smartphones can also be used as credentials in conjunction with access software running on mobile devices.
[8] In addition to older more traditional card access technologies, newer technologies such as near-field communication (NFC), Bluetooth low energy or Ultra-wideband (UWB) can also communicate user credentials to readers for system or building access.
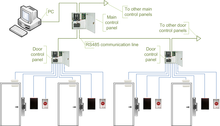
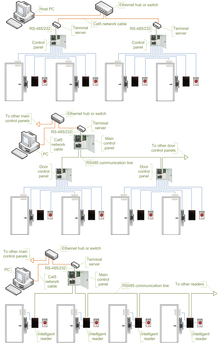
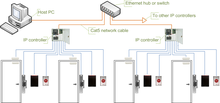
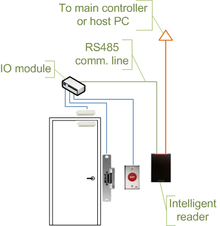
The controllers are IP enabled, and connect to a host and database using standard networks[13] Access control readers may be classified by the functions they are able to perform:[14] Some readers may have additional features such as an LCD and function buttons for data collection purposes (i.e. clock-in/clock-out events for attendance reports), camera/speaker/microphone for intercom, and smart card read/write support.
Controllers are connected to a host PC via a serial RS-485 communication line (or via 20mA current loop in some older systems).
External RS-232/485 converters or internal RS-485 cards have to be installed, as standard PCs do not have RS-485 communication ports.
Only if the connection to the main controller is unavailable, will the readers use their internal database to make access decisions and record events.
Semi-intelligent reader that have no database and cannot function without the main controller should be used only in areas that do not require high security.
In spite of the rapid development and increasing use of computer networks, access control manufacturers remained conservative, and did not rush to introduce network-enabled products.
When pressed for solutions with network connectivity, many chose the option requiring less efforts: addition of a terminal server, a device that converts serial data for transmission via LAN or WAN.
The same advantages and disadvantages apply, but the on-board network interface offers a couple of valuable improvements.
The most common security risk of intrusion through an access control system is by simply following a legitimate user through a door, and this is referred to as tailgating.
This risk can be minimized through security awareness training of the user population or more active means such as turnstiles.
In very high-security applications this risk is minimized by using a sally port, sometimes called a security vestibule or mantrap, where operator intervention is required presumably to assure valid identification.
This is relatively difficult on properly secured doors with strikes or high holding force magnetic locks.
Fully implemented access control systems include forced door monitoring alarms.
These vary in effectiveness, usually failing from high false positive alarms, poor database configuration, or lack of active intrusion monitoring.
In order to mitigate risk from natural disasters, the structure of the building, down to the quality of the network and computer equipment vital.
A strong magnet can operate the solenoid controlling bolts in electric locking hardware.
The hacker simply walks by the user, reads the card, and then presents the number to a reader securing the door.
Many access control credentials unique serial numbers are programmed in sequential order during manufacturing.
Ordering credentials with random unique serial numbers is recommended to counter this threat.
[citation needed] In computer security, general access control includes authentication, authorization, and audit.
[citation needed] Although some systems equate subjects with user IDs, so that all processes started by a user by default have the same authority, this level of control is not fine-grained enough to satisfy the principle of least privilege, and arguably is responsible for the prevalence of malware in such systems (see computer insecurity).