Block cipher
In his seminal 1949 publication, Communication Theory of Secrecy Systems, Claude Shannon analyzed product ciphers and suggested them as a means of effectively improving security by combining simple operations such as substitutions and permutations.
[6] Iterated product ciphers carry out encryption in multiple rounds, each of which uses a different subkey derived from the original key.
[11] The publication of the DES cipher by the United States National Bureau of Standards (subsequently the U.S. National Institute of Standards and Technology, NIST) in 1977 was fundamental in the public understanding of modern block cipher design.
At the beginning and the end, the data is modified with key material (often with XOR): Given one of the standard iterated block cipher design schemes, it is fairly easy to construct a block cipher that is cryptographically secure, simply by using a large number of rounds.
Further, a good block cipher is designed to avoid side-channel attacks, such as branch prediction and input-dependent memory accesses that might leak secret data via the cache state or the execution time.
[14] The non-linear substitution stage mixes the key bits with those of the plaintext, creating Shannon's confusion.
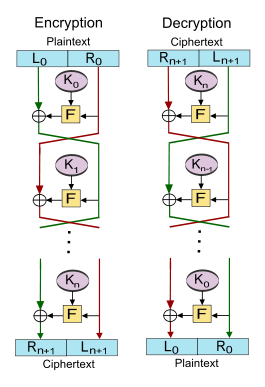
[19] In a Feistel cipher, the block of plain text to be encrypted is split into two equal-sized halves.
Many authors draw an ARX network, a kind of data flow diagram, to illustrate such a round function.
[23] To overcome this limitation, several so-called block cipher modes of operation have been designed[24][25] and specified in national recommendations such as NIST 800-38A[26] and BSI TR-02102[27] and international standards such as ISO/IEC 10116.
[28] The general concept is to use randomization of the plaintext data based on an additional input value, frequently called an initialization vector, to create what is termed probabilistic encryption.
[29] In the popular cipher block chaining (CBC) mode, for encryption to be secure the initialization vector passed along with the plaintext message must be a random or pseudo-random value, which is added in an exclusive-or manner to the first plaintext block before it is encrypted.
While many popular schemes described in standards and in the literature have been shown to be vulnerable to padding oracle attacks,[31][32] a solution that adds a one-bit and then extends the last block with zero-bits, standardized as "padding method 2" in ISO/IEC 9797-1,[33] has been proven secure against these attacks.
[32] This property results in the cipher's security degrading quadratically, and needs to be taken into account when selecting a block size.
[37] Integral cryptanalysis is a cryptanalytic attack that is particularly applicable to block ciphers based on substitution–permutation networks.
Unlike differential cryptanalysis, which uses pairs of chosen plaintexts with a fixed XOR difference, integral cryptanalysis uses sets or even multisets of chosen plaintexts of which part is held constant and another part varies through all possibilities.
Note, however, that making statements like this requires formal mathematical definitions for what it means for an encryption algorithm or a block cipher to "be secure".
If in Step 2 above adversaries have the option of learning f−1(X) instead of f(X) (but still have only small advantages) then E is a strong PRP (SPRP).
Equivalently, if PE(A) is small for all relevant A, then no attacker has a significant probability of winning the new game.
Common factors include:[39][40] Lucifer is generally considered to be the first civilian block cipher, developed at IBM in the 1970s based on work done by Horst Feistel.
DES prompted a large amount of other work and publications in cryptography and cryptanalysis in the open community and it inspired many new cipher designs.
As time went on, its inadequacy became apparent, especially after a special-purpose machine designed to break DES was demonstrated in 1998 by the Electronic Frontier Foundation.
[43] The International Data Encryption Algorithm (IDEA) is a block cipher designed by James Massey of ETH Zurich and Xuejia Lai; it was first described in 1991, as an intended replacement for DES.
IDEA derives much of its security by interleaving operations from different groups – modular addition and multiplication, and bitwise exclusive or (XOR) – which are algebraically "incompatible" in some sense.
The designers analysed IDEA to measure its strength against differential cryptanalysis and concluded that it is immune under certain assumptions.
The original suggested choice of parameters was a block size of 64 bits, a 128-bit key, and 12 rounds.
A key feature of RC5 is the use of data-dependent rotations; one of the goals of RC5 was to prompt the study and evaluation of such operations as a cryptographic primitive.
The tantalizing simplicity of the algorithm together with the novelty of the data-dependent rotations has made RC5 an attractive object of study for cryptanalysts.
The Rijndael cipher developed by Belgian cryptographers, Joan Daemen and Vincent Rijmen was one of the competing designs to replace DES.
Notable features of the design include the key-dependent S-boxes and a highly complex key schedule.
This makes format-preserving encryption schemes a natural generalization of (tweakable) block ciphers.