Security alarm
If a potential intruder tries to enter into a house, they test whether it is closed and locked, uses tools on openings, or/and applies pressure, creating low-frequency sound vibrations.
These barriers are immune to harsh weather, such as fog, heavy rain, snow and sandstorms: none of these atmospheric phenomena affect in any way the behaviour and the reliability of the microwave detection.
[4] The more recent and higher performance models of these detectors generate a detection whether the intruder is rolling, crossing, crawling or moving very slow within the electromagnetic field[5] reducing false alarms.
The ellipsoidal shape of the longitudinal section however does not allow a good detection capability close to the receiver or transmitter heads, and those areas are commonly referred to as "dead zones".
They are similar to microwave detectors but can detect the precise location and a GPS coordinate of intruders in areas extending over hundreds of acres.
This target information is typically displayed on a map, user interface or situational awareness software that defines geographical alert zones or geofences with different types of actions initiated depending on time of day and other factors.
The technology can be an effective long-range detection system, if installed in stacks of three or more where the transmitters and receivers are staggered to create a fence-like barrier.
[11] The current technology allows to realize suspended silicon structures that are attached to the substrate in some points called anchors, and that constitute the sensitive mass of the accelerometer MEMS.
MEMS accelerometers’ significant advantages also stem from their small size and high measurement frequency; additionally, they can be integrated with multiple sensors with different functions.
[17] This type of sensor can be used to detect intruders carrying substantial amounts of metal, such as a firearm, making it ideally suited for anti-poaching applications.
[18] Sometimes referred to as E-field, this volumetric sensor uses Electric field proximity sensing and can be installed on buildings, perimeters, fences, and walls.
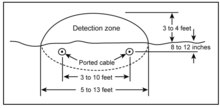
Microphonic systems vary in design (for example, time-domain reflectrometer or piezo-electric) but each is generally based on the detection of an intruder attempting to cut or climb over a fence.
Unwanted alarms caused by birds and other animals can be avoided by adjusting the sensors to ignore objects that exert small amounts of pressure on the wires.
However, despite performing in a similar manner to microphonic-based systems, fiber optic cables have higher cost and is more complex due to the use of fiber-optic technology.
When the change in field strength weakens due to the presence of an object and reaches a pre-set lower threshold, an alarm condition is generated.
The trigger signal from sensors are transmitted to one or more control units either through wires or wireless means, such as radio, line carrier, and infrared.
In rural areas where not many may hear the fire bell or burglar siren, lights or sounds may not make much difference, as the nearest emergency responders may arrive too late to avoid losses.
Direct connections are now most usually seen only in federal, state, and local government buildings, or on a school campus that has a dedicated security, police, fire, or emergency medical department.
The company offered an alternative to existing alarm signaling while setting the current standard for professional dual path security monitoring.
For actual break-ins, the speaker phones allow the central station to urge the intruder to cease and desist as response units have been dispatched.
High-security alarms may require multiple codes, or a fingerprint, badge, hand-geometry, retinal scan, encrypted-response generator, and other means that are deemed sufficiently secure for the purpose.
[21] In many municipalities across the United States, policies have been adopted to fine home and business owners for multiple false alarm activations from their security system.
The source audio and video streams are sent over a communication link, usually an Internet protocol (IP) network, to the central station where monitors retrieve the images through proprietary software.
The information is then relayed to law enforcement and recorded to an event file, which can be used to plan a more strategic and tactical approach of a property, and later as prosecution evidence.
When a signal is received, a trained monitoring professional accesses the on-site digital video recorder (DVR) through an IP link to determine the cause of the activation.
Enhanced call verification (ECV) helps reduce false dispatches while still protecting citizens, and is mandated in several US jurisdictions, although the alarm industry has successfully opposed it in others.
[21] ECV requires central station personnel to attempt to verify the alarm activation by making a minimum of two phone calls to two different responsible party telephone numbers before dispatching law enforcement to the scene.
The secondary number, best practices dictate, should be to a telephone that is answered even after hours, preferably a cellular phone of a decision maker authorized to request or bypass emergency response.
ECV, as it cannot confirm an actual intrusion event and will not prompt a priority law enforcement dispatch, is not considered true alarm verification by the security industry.
With the use of the Internet or radio path and a compatible IP/radio transmitting device (at the alarmed premises), some checks can now be carried out remotely from the central station.