Cipher suite
[2] The structure and use of the cipher suite concept are defined in the TLS standard document.
[4] The use of ciphers has been a part of the Secure Socket Layer (SSL) transit protocol since its creation.
Instead the ability for a client and a server to choose from a small set of ciphers to secure their connection was called Cipher-Choice.
Each cipher suite has a unique name that is used to identify it and to describe the algorithmic contents of it.
Each segment in a cipher suite name stands for a different algorithm or protocol.
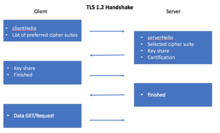
In response, the server sends a serverHello message that includes the chosen cipher suite and the session ID.
After successfully verifying the authentication of the server and, if needed, exchanging the secret key, the client sends a finished message to signal that it is done with the handshake process.
First the client sends a clientHello message to the server that contains a list of supported ciphers in order of the client's preference and makes a guess on what key algorithm is being used so that it can send a secret key to share if needed.
After receiving the clientHello, the server sends a serverHello with its key, a certificate, the chosen cipher suite and the finished message.
Instead, all TLS parameter registries now include the flag DTLS-OK to signal if a cipher suite supports DTLS.
If the connection fails, it will automatically retry again with a lower protocol such as TLS 1.0 or SSL 3.0 until the handshake is successful with the server.
However, it is possible for an adversary to take advantage of this feature and make it so that a client will automatically downgrade to a version of TLS or SSL that supports cipher suites with algorithms that are known for weak security and vulnerabilities.
One way to avoid this security flaw is to disable the ability of a server or client to be able to downgrade to SSL 3.0.
If SSL 3.0 support is needed for legacy hardware, there is an approved TLS_FALLBACK_SCSV cipher suite which verifies that downgrades are not triggered for malicious intentions.
[17] Encryption, key exchange and authentication algorithms usually require a large amount of processing power and memory.
Two examples include: Each of these cipher suites has been implemented to run on devices with constraints in processing power and memory.
Implementations of the pre-shared key cipher suite used only 1889 bytes of RAM and 38266 of flash ROM which is very resource-conscious compared to most encryption and security algorithms.