Clandestine cell system
This limits the harm that can be done to the organization as a whole by any individual cell member defecting, being a mole, being surveilled, or giving up information after being apprehended and interrogated.
The structure of a clandestine cell system can range from a strict hierarchy to an extremely distributed organization, depending on the group's ideology, its operational area, the communications technologies available, and the nature of the mission.
Criminal organizations, undercover operations, and unconventional warfare units led by special forces may also use this sort of organizational structure.
If the team was to carry out direct action (often an unwise mission unless an appreciable number of the locals had military experience) it would be necessary to assemble into larger units for combat.
The legitimacy of the Jedburgh team came from its known affiliation with Allied powers, and it was a structure more appropriate for unconventional warfare than for truly clandestine operations[clarify].
Also known as the Viet Cong, this organization grew from earlier anticolonial groups fighting the French and from anti-Japanese guerrillas during World War II.
The IRA[clarify] had an extensive network of inactive or sleeper cells, so it could summon new ad hoc organizations for any specific operation.
[6] In such a split organization, public issues can be addressed overtly while military actions are kept covert and intelligence functions stay clandestine.
This can include leaders, trainers, and supplies (such as the Jedburgh assistance to the French Resistance), or a safe haven for overt activities (such as the NLF spokesmen who could operate in Hanoi).
Early U.S. support to the Afghan Northern Alliance against the Taliban used clandestine operators from the CIA and United States Army Special Forces.
Note that both unconventional warfare (guerrilla operations) and foreign internal defense (counterinsurgency) may be covert and use cellular organization.
In a covert counterinsurgency mission, only selected host nation leaders are aware of the foreign support organization.
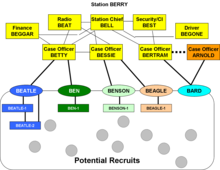
Cryptonyms begin with a two-letter country or subject name (e.g., AL), followed by more letters so as to form an arbitrary word, such as "BERRY", "BEN", and "BEATLE" in the example below.
Assume that in team ALAN, ALASTAIR is one of the officers with local contacts, and might recruit two cell leaders: ALPINE and ALTITUDE.
The legitimacy[clarify] of the subcell structure came from the recruitment process, originally by the case officer and then by the cell leaders.
[citation needed] If the al-Qaeda Training Manual[13] is authentic, it demonstrates that Eastern cell structures may differ from the Western mode.
Al-Qaeda's minimal core leadership group can be viewed as a ring or chain network, with each leader/node heading their own particular hierarchy.
Trust and personal relationships are an essential part of the Al-Qaeda network (a limiting factor[clarify], even while it provides enhanced security).
Members of outer cells and support systems might know him only as "the Commander", or, as in the actual case of al-Qaeda, Osama bin Laden's face is recognizable worldwide, but only a few people knew where he was or even how to contact him.
Some of these functions, such as finance, are far harder to operate in remote areas (like the FATA of Pakistan) than in cities with large numbers of official and unofficial financial institutions and the communications to support them.
If the financial office is distant from the remote headquarters, there is a need for couriers, who must be trusted to some extent, but who may not know the contents of their messages or the actual identity of the sender and/or receiver.
Military leaders might have direct, possibly one-way, communications with their cells, or they might have to give Kim the messages to be transmitted, by means that Anton and Hassan have no need to know.
[clarify] The security structure also means that Hassan does not know the members of Anton's cells, and Kim may know only ways to communicate with them but not their identity.
If al-Qaeda uses its typical modus operandi of multiple concurrent attacks, there may be an operational cell for each target location.
special operations forces sometimes wait for presidential authorization to make an attack, or even to move to staging areas.
A country would have to face the consequences of an inappropriate attack, so it may tend to be overcautious, whereas a terror network might merely shrug at the world being upset.
If their cells need constant control, there are communications links that might be detected by SIGINT, and if their command can be disrupted, the field units could not function.
Since there is fairly little downside for terrorists to attack out of synchronization with other activities, the lack of positive control becomes a strength of their approach to cell organization.
Al-Qaeda's approach differs from that of earlier terrorist organizations: In the above graphic, note the indirect support network controlled by Richard's subcell.
"[18] Indeed, once intelligence learns the name and characteristics of an at-large adversary, as well as some sensitive information that would plausibly be known to him, a news release could be issued to talk about his cooperation.