Equation Group
[1][2][3] Kaspersky Labs describes them as one of the most sophisticated cyber attack groups in the world and "the most advanced (...) we have seen", operating alongside the creators of Stuxnet and Flame.
By 2015, Kaspersky documented 500 malware infections by the group in at least 42 countries, while acknowledging that the actual number could be in the tens of thousands due to its self-terminating protocol.
[10]: 13 They also identified that the platform had at times been spread by interdiction (interception of legitimate CDs sent by a scientific conference organizer by mail),[10]: 15 and that the platform had the "unprecedented" ability to infect and be transmitted through the hard drive firmware of several major hard drive manufacturers, and create and use hidden disk areas and virtual disk systems for its purposes, a feat which would require access to the manufacturer's source code to achieve,[10]: 16–18 and that the tool was designed for surgical precision, going so far as to exclude specific countries by IP and allow targeting of specific usernames on discussion forums.
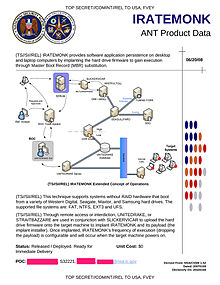
[4] F-Secure claims that the Equation Group's malicious hard drive firmware is TAO program "IRATEMONK",[13] one of the items from the NSA ANT catalog exposed in a 2013 Der Spiegel article.
IRATEMONK provides the attacker with an ability to have their software application persistently installed on desktop and laptop computers, despite the disk being formatted, its data erased or the operating system re-installed.
[16] The most recent dates of the stolen files are from June 2013, thus prompting Edward Snowden to speculate that a likely lockdown resulting from his leak of the NSA's global and domestic surveillance efforts stopped The Shadow Brokers' breach of the Equation Group.