Heartbleed
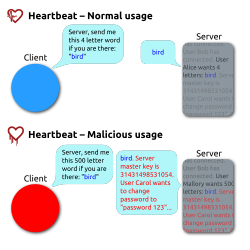
It resulted from improper input validation (due to a missing bounds check) in the implementation of the TLS heartbeat extension.
[7] The federal Canadian Cyber Incident Response Centre issued a security bulletin advising system administrators about the bug.
The report also broke the devices down by 10 other categories such as organization (the top 3 were wireless companies), product (Apache httpd, Nginx), and service (HTTPS, 81%).
Forbes cybersecurity columnist Joseph Steinberg wrote:Some might argue that Heartbleed is the worst vulnerability found (at least in terms of its potential impact) since commercial traffic began to flow on the Internet.
[40]The Sydney Morning Herald published a timeline of the discovery on 15 April 2014, showing that some organizations had been able to patch the bug before its public disclosure.
Netcraft stated:By reusing the same private key, a site that was affected by the Heartbleed bug still faces exactly the same risks as those that have not yet replaced their SSL certificates.
[47] The Canada Revenue Agency reported a theft of social insurance numbers belonging to 900 taxpayers, and said that they were accessed through an exploit of the bug during a 6-hour period on 8 April 2014.
For example, on 12 April 2014, at least two independent researchers were able to steal private keys from an experimental server intentionally set up for that purpose by CloudFlare.
[57] In August 2014, it was made public that the Heartbleed vulnerability enabled hackers to steal security keys from Community Health Systems, the second-biggest for-profit U.S. hospital chain in the United States, compromising the confidentiality of 4.5 million patient records.
[58] Many major web sites patched the bug or disabled the Heartbeat Extension within days of its announcement,[59] but it is unclear whether potential attackers were aware of it earlier and to what extent it was exploited.
[citation needed] Based on examinations of audit logs by researchers, it has been reported that some attackers may have exploited the flaw for at least five months before discovery and announcement.
[60][61] Errata Security pointed out that a widely used non-malicious program called Masscan, introduced six months before Heartbleed's disclosure, abruptly terminates the connection in the middle of handshaking in the same way as Heartbleed, generating the same server log messages, adding "Two new things producing the same error messages might seem like the two are correlated, but of course, they aren't.
[62]" According to Bloomberg News, two unnamed insider sources informed it that the United States' National Security Agency had been aware of the flaw since shortly after its appearance but—instead of reporting it—kept it secret among other unreported zero-day vulnerabilities in order to exploit it for the NSA's own purposes.
[67] The allegation prompted the American government to make, for the first time, a public statement on its zero-day vulnerabilities policy, accepting the recommendation of the review group's 2013 report that had asserted "in almost all instances, for widely used code, it is in the national interest to eliminate software vulnerabilities rather than to use them for US intelligence collection", and saying that the decision to withhold should move from the NSA to the White House.
Because of this failure to do proper bounds checking, the message returned consists of the payload, possibly followed by whatever else happened to be in the allocated memory buffer.
Moreover, the confidential data exposed could include authentication secrets such as session cookies and passwords, which might allow attackers to impersonate a user of the service.
Although the bug received more attention due to the threat it represents for servers,[80] TLS clients using affected OpenSSL instances are also vulnerable.
[84] An analysis posted on GitHub of the most visited websites on 8 April 2014 revealed vulnerabilities in sites including Yahoo!, Imgur, Stack Overflow, Slate, and DuckDuckGo.
[85][86] The following sites have services affected or made announcements recommending that users update passwords in response to the bug: The Canadian federal government temporarily shut online services of the Canada Revenue Agency (CRA) and several government departments over Heartbleed bug security concerns.
[113][114] Another Canadian Government agency, Statistics Canada, had its servers compromised due to the bug and also temporarily took its services offline.
[108] The servers of LastPass were vulnerable,[116] but due to additional encryption and forward secrecy, potential attacks were not able to exploit this bug.
[118][119][120][121] Game-related services including Steam, Minecraft, Wargaming, League of Legends, GOG.com, Origin, Sony Online Entertainment, Humble Bundle, and Path of Exile were affected and subsequently fixed.
Validation of signatures and the legitimacy of other authentications made with a potentially compromised key (such as client certificate use) must be done with regard to the specific system involved.
On the first aspect, Merkel mentions the use of the C programming language as one risk factor which favored Heartbleed's appearance, echoing Wheeler's analysis.
[180][181] On the same aspect, Theo de Raadt, founder and leader of the OpenBSD and OpenSSH projects, has criticized the OpenSSL developers for writing their own memory management routines and thereby, he claims, circumventing OpenBSD C standard library exploit countermeasures, saying "OpenSSL is not developed by a responsible team.
[185] The author of the change which introduced Heartbleed, Robin Seggelmann,[186] stated that he missed validating a variable containing a length and denied any intention to submit a flawed implementation.
[188] Software engineer John Walsh commented: Think about it, OpenSSL only has two [fulltime] people to write, maintain, test, and review 500,000 lines of business critical code.
"[189] David A. Wheeler described audits as an excellent way to find vulnerabilities in typical cases, but noted that "OpenSSL uses unnecessarily complex structures, which makes it harder to both humans and machines to review."
[3] After learning about donations for the 2 or 3 days following Heartbleed's disclosure totaling US$841, Kaminsky commented "We are building the most important technologies for the global economy on shockingly underfunded infrastructure.
[195] The initiative intends to allow lead developers to work full time on their projects and to pay for security audits, hardware and software infrastructure, travel, and other expenses.