RADIUS
RADIUS was developed by Livingston Enterprises in 1991 as an access server authentication and accounting protocol.
[3] RADIUS is an AAA (authentication, authorization, and accounting) protocol that manages network access.
The credentials are passed to the NAS device via the link-layer protocol—for example, Point-to-Point Protocol (PPP) in the case of many dialup or DSL providers or posted in an HTTPS secure web form.
[4] This request includes access credentials, typically in the form of username and password or security certificate provided by the user.
The RADIUS server checks that the information is correct using authentication schemes such as PAP, CHAP or EAP.
Historically, RADIUS servers checked the user's information against a locally stored flat file database.
Modern RADIUS servers can do this, or can refer to external sources—commonly SQL, Kerberos, LDAP, or Active Directory servers—to verify the user's credentials.
Each of these three RADIUS responses may include a Reply-Message attribute which may give a reason for the rejection, the prompt for the challenge, or a welcome message for the accept.
"Start" records typically contain the user's identification, network address, point of attachment and a unique session identifier.
Finally, when the user's network access is closed, the NAS issues a final Accounting Stop record (a RADIUS Accounting Request packet containing an Acct-Status-Type attribute with the value "stop") to the RADIUS server, providing information on the final usage in terms of time, packets transferred, data transferred, reason for disconnect and other information related to the user's network access.
Typically, the client sends Accounting-Request packets until it receives an Accounting-Response acknowledgement, using some retry interval.
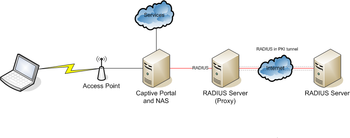
Some of advantages of using proxy chains include scalability improvements, policy implementations and capability adjustments.
But in roaming scenarios, the NAS, Proxies and Home Server could be typically managed by different administrative entities.
More generally, some roaming partners establish a secure tunnel between the RADIUS servers to ensure that users' credentials cannot be intercepted while being proxied across the internet.
The fields are transmitted from left to right, starting with the code, the identifier, the length, the authenticator and the attributes.
Assigned RADIUS Codes (decimal) include the following:[9] The Identifier field aids in matching requests and replies.
The RADIUS Attribute Value Pairs (AVP) carry data in both the request and the response for the authentication, authorization, and accounting transactions.
The RADIUS protocol transmits obfuscated passwords using a shared secret and the MD5 hashing algorithm.
Additionally, the user's security credentials are the only part protected by RADIUS itself, yet other user-specific attributes such as tunnel-group IDs or VLAN memberships passed over RADIUS may be considered sensitive (helpful to an attacker) or private (sufficient to identify the individual client) information as well.
As more dial-up customers used the NSFNET a request for proposal was sent out by Merit Network in 1991 to consolidate their various proprietary authentication, authorization and accounting systems.
Livingston Enterprises was acquired by Lucent Technologies and together with Merit steps were taken to gain industry acceptance for RADIUS as a protocol.
Accounting records can be written to text files, various databases, forwarded to external servers, etc.