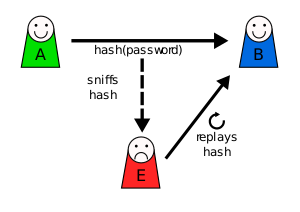
Replay attack
[1] This is carried out either by the originator or by an adversary who intercepts the data and re-transmits it, possibly as part of a spoofing attack by IP packet substitution.
In this case, an attacker would be unable to perform the replay because on a new run the session ID would have changed.
Bob can also send nonces but should then include a message authentication code (MAC), which Alice should check.
However, the Kerberos protocol, as implemented in Microsoft Windows Active Directory, includes the use of a scheme involving time stamps to severely limit the effectiveness of replay attacks.
Many vehicles on the road use a remote keyless system, or key fob, for the convenience of the user.
This attack is performed by placing a device that can receive and transmit radio waves within range of the target vehicle.
The transmitter will attempt to jam any RF vehicle unlock signal while receiving it and placing it in a buffer for later use.
[11] In the realm of smart home environments, Internet of Things (IoT) devices are increasingly vulnerable to replay attacks, where an adversary intercepts and replays legitimate communication signals between an IoT device and its companion app.
These attacks can compromise a wide array of devices, including smart plugs, security cameras, and even household appliances.
A recent study[12] demonstrated that a substantial portion of consumer IoT devices are prone to replay attacks.
Researchers found that 75% of tested devices supporting local connectivity were vulnerable to such attacks.
These vulnerabilities allow attackers to mimic legitimate commands, potentially enabling unauthorized actions such as turning on a smart kettle, unlocking doors, or manipulating security systems.
Such breaches pose significant safety, security, and privacy risks, as malicious actors can gain control over critical home systems.