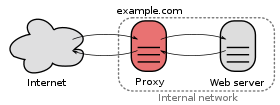
Reverse proxy
An important advantage of doing so is that the web servers can be hidden behind a firewall on a company-internal network, and only the reverse proxy needs to be directly exposed to the Internet.
Large websites and content delivery networks use reverse proxies, together with other techniques, to balance the load between internal servers.
Proxy caches of this sort can often satisfy a considerable number of website requests, greatly reducing the load on the origin server(s).
In a technique named "spoon-feeding",[4] a dynamically generated page can be produced all at once and served to the reverse proxy, which can then return it to the client a little bit at a time.
The program that generates the page need not remain open, thus releasing server resources during the possibly extended time the client requires to complete the transfer.
This requires the proxy to possess the TLS certificate and its corresponding private key, extending the number of systems that can have access to non-encrypted data and making it a more valuable target for attackers.
Applications that were developed for the internal use of a company are not typically hardened to public standards and are not necessarily designed to withstand all hacking attempts.
When an organisation allows external access to such internal applications via a reverse proxy, they might unintentionally increase their own attack surface and invite hackers.