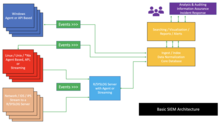
Security information and event management
[3] SIEM technology collects and aggregates data from various systems, allowing organizations to meet compliance requirements while safeguarding against threats.
The integration of SIM and SEM within SIEM provides organizations with a centralized approach for monitoring security events and responding to threats in real-time.
First introduced by Gartner analysts Mark Nicolett and Amrit Williams in 2005, the term SIEM has evolved to incorporate advanced features such as threat intelligence and behavioral analytics, which allow SIEM solutions to manage complex cybersecurity threats, including zero-day vulnerabilities and polymorphic malware.
For instance, Executive Order 14028 signed in 2021 by U.S. President Joseph Biden mandates the use of SIEM technologies to improve incident detection and reporting in federal systems.
Compliance with these mandates is further reinforced by frameworks such as NIST SP 800-92, which outlines best practices for managing computer security logs.
Starting in the late 1970s, working groups began establishing criteria for managing auditing and monitoring programs, laying the groundwork for modern cybersecurity practices, such as insider threat detection and incident response.
[6] In 2005, the term "SIEM" (Security Information and Event Management) was introduced by Gartner analysts Mark Nicolett and Amrit Williams.
Cybersecurity professionals now rely on logging data to perform real-time security functions, driven by governance models that incorporate these processes into analytical tasks.
By reinforcing information assurance controls within RMFs, the order aimed to drive compliance and secure funding for cybersecurity initiatives.
[9][10] Although the guide is not exhaustive due to rapid changes in technology since its publication, it remains relevant by anticipating industry growth.
NIST is not the only source of guidance on regulatory mechanisms for auditing and monitoring, and many organizations are encouraged to adopt SIEM solutions rather than relying solely on host-based checks.
Federal systems categorized based on their impact on confidentiality, integrity, and availability (CIA) have five specific logging requirements (AU-2 a-e) that must be met.
These controls, supported by SIEM solutions, help ensure continuous monitoring, risk assessments, and in-depth defense mechanisms across federal and private networks.
Computer security researcher Chris Kubecka identified the following SIEM use cases, presented at the hacking conference 28C3 (Chaos Communication Congress).
For example automated response capabilities of the Singularity™ AI SIEM, including autonomous quarantine of malicious files and termination of harmful processes.
Alongside the time, the system may often record other useful information such as the device used, physical location, IP address, incorrect login attempts, etc.
With suitable correlation rules in place, a SIEM should trigger an alert at the start of the attack so that the company can take the necessary precautionary measures to protect vital systems.