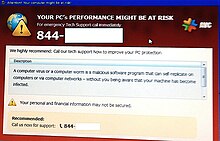
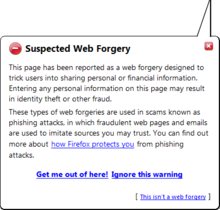
Phishing
Phishing is a form of social engineering and a scam where attackers deceive people into revealing sensitive information[1] or installing malware such as viruses, worms, adware, or ransomware.
[11] Phishing attacks, often delivered via email spam, attempt to trick individuals into giving away sensitive information or login credentials.
[12] The goal of the attacker can vary, with common targets including financial institutions, email and cloud productivity providers, and streaming services.
[15] This type of social engineering attack can involve sending fraudulent emails or messages that appear to be from a trusted source, such as a bank or government agency.
[36][37] When victims scan the QR code with their phone or device, they are redirected to a fake website designed to steal personal information, login credentials, or financial details.
[34] As QR codes become more widely used for things like payments, event check-ins, and product information, quishing is emerging as a significant concern for digital security.
Users are advised to exercise caution when scanning unfamiliar QR codes and ensure they are from trusted sources, although the UK's National Cyber Security Centre rates the risk as far lower than other types of lure.
To check the destination of a link, many email clients and web browsers will show the URL in the status bar when the mouse is hovering over it.
[46] Phishing often uses social engineering techniques to trick users into performing actions such as clicking a link or opening an attachment, or revealing sensitive information.
It often involves pretending to be a trusted entity and creating a sense of urgency,[47] like threatening to close or seize a victim's bank or insurance account.
[50] Early phishing techniques can be traced back to the 1990s, when black hat hackers and the warez community used AOL to steal credit card information and commit other online crimes.
The term "phishing" is said to have been coined by Khan C. Smith, a well-known spammer and hacker,[51] and its first recorded mention was found in the hacking tool AOHell, which was released in 1994.
AOHell allowed hackers to impersonate AOL staff and send instant messages to victims asking them to reveal their passwords.
[81][82] In August 2016, members of the Bundestag and political parties such as Linken-faction leader Sahra Wagenknecht, Junge Union, and the CDU of Saarland were targeted by spear-phishing attacks suspected to be carried out by Fancy Bear.
In August 2016, the World Anti-Doping Agency reported the receipt of phishing emails sent to users of its database claiming to be official WADA, but consistent with the Russian hacking group Fancy Bear.
In this case, a 17-year-old hacker and accomplices set up a fake website resembling Twitter's internal VPN provider used by remote working employees.
Posing as helpdesk staff, they called multiple Twitter employees, directing them to submit their credentials to the fake VPN website.
One example is a study by the National Library of Medicine, in which an organization received 858,200 emails during a 1-month testing period, with 139,400 (16%) being marketing and 18,871 (2%) being identified as potential threats.
Emails from banks and credit card companies often include partial account numbers, but research has shown that people tend to not differentiate between the first and last digits.
[109] Web browsers such as Google Chrome, Internet Explorer 7, Mozilla Firefox 2.0, Safari 3.2, and Opera all contain this type of anti-phishing measure.
[115] According to a report by Mozilla in late 2006, Firefox 2 was found to be more effective than Internet Explorer 7 at detecting fraudulent sites in a study by an independent software testing company.
[122][123] In addition, this feature (like other forms of two-factor authentication) is susceptible to other attacks, such as those suffered by Scandinavian bank Nordea in late 2005,[124] and Citibank in 2006.
Unlike the static images used on the Bank of America website, a dynamic image-based authentication method creates a one-time passcode for the login, requires active participation from the user, and is very difficult for a phishing website to correctly replicate because it would need to display a different grid of randomly generated images that includes the user's secret categories.
On January 26, 2004, the U.S. Federal Trade Commission filed the first lawsuit against a Californian teenager suspected of phishing by creating a webpage mimicking America Online and stealing credit card information.
[139] UK authorities jailed two men in June 2005 for their role in a phishing scam,[140] in a case connected to the U.S. Secret Service Operation Firewall, which targeted notorious "carder" websites.
[141] In 2006, Japanese police arrested eight people for creating fake Yahoo Japan websites, netting themselves ¥100 million (US$870,000)[142] and the FBI detained a gang of sixteen in the U.S. and Europe in Operation Cardkeeper.
This bill aimed to impose fines of up to $250,000 and prison sentences of up to five years on criminals who used fake websites and emails to defraud consumers.
March 2005 also saw a partnership between Microsoft and the Australian government teaching law enforcement officials how to combat various cyber crimes, including phishing.
He was found guilty of sending thousands of emails to AOL users, while posing as the company's billing department, which prompted customers to submit personal and credit card information.
Facing a possible 101 years in prison for the CAN-SPAM violation and ten other counts including wire fraud, the unauthorized use of credit cards, and the misuse of AOL's trademark, he was sentenced to serve 70 months.