Spoofing attack
[1] Many of the protocols in the TCP/IP suite do not provide mechanisms for authenticating the source or destination of a message,[2] leaving them vulnerable to spoofing attacks when extra precautions are not taken by applications to verify the identity of the sending or receiving host.
According to a study by GlobalWebIndex, 49% of global VPN users utilize VPNs primarily to access territorially restricted entertainment content.
[12] This means that spoofed signals may be modified in such a way as to cause the receiver to estimate its position to be somewhere other than where it actually is, or to be located where it is but at a different time, as determined by the attacker.
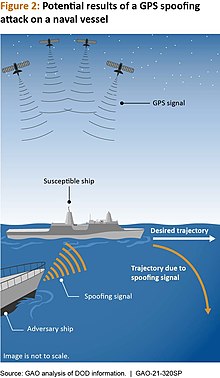
[14][15][16] However, seeing as more than 80% of global trade is moved through shipping companies, relying upon GNSS systems for navigation is necessary even though maritime vessels will be vulnerable to spoofing attacks with limited countermeasures.
[17][18] All GNSS systems, such as the US GPS, Russia's GLONASS, China's BeiDou, and Europe's Galileo constellation, are vulnerable to this technique.
[28] On October 15, 2023, Israel Defense Forces (IDF) announced that GPS had been “restricted in active combat zones in accordance with various operational needs,” but has not publicly commented on more advanced interference.
In April 2024, however, researchers at University of Texas at Austin detected false signals and traced their origin to a particular air base in Israel run by the IDF.
[29] In June 2017, approximately twenty ships in the Black Sea complained of GPS anomalies, showing vessels to be transpositioned miles from their actual location, in what Professor Todd Humphreys believed was most likely a spoofing attack.
[32] Incidents involving Russian GPS spoofing include during a November 2018 NATO exercise in Finland that led to ship collision (unconfirmed by authorities).
Some of the most important and most recommended to use are:[37] These installation and operation strategies and development opportunities can significantly enhance the ability of GPS receivers and associated equipment to defend against a range of interference, jamming, and spoofing attacks.
[citation needed] A method proposed by researchers from the Department of Electrical and Computer Engineering at the University of Maryland, College Park and the School of Optical and Electronic Information at Huazhong University of Science and Technology that aims to help mitigate the effects of GNSS spoofing attacks by using data from a vehicles controller area network (CAN) bus.
Properties such as the vehicles speed and steering angle would be amalgamated and regression modeled in order to achieve a minimum error in position of 6.25 meters.
[41] Technologies related to the synthesis and modeling of speech are developing very quickly, allowing one to create voice recordings almost indistinguishable from real ones.
[42] However, an early study has shown that feature design and masking augmentation have a significant impact on the ability to detect spoofed voice.
[43] Facial recognition technology is widely employed in various areas, including immigration checks and phone security, as well as on popular platforms like Airbnb and Uber to verify individuals' identities.
Some online sources and tutorials detail methods for tricking facial recognition systems through practices known as face spoofing or presentation attacks, which can pose risks in terms of unauthorized access.