Stuxnet
[2] Although neither country has openly admitted responsibility, multiple independent news organizations recognize Stuxnet to be a cyberweapon built jointly by the United States and Israel in a collaborative effort known as Operation Olympic Games.
[2] Stuxnet's design and architecture are not domain-specific and it could be tailored as a platform for attacking modern SCADA and PLC systems (e.g., in factory assembly lines or power plants), most of which are in Europe, Japan and the United States.
[12][13] Stuxnet, discovered by Sergey Ulasen from a Belarussian antivirus company VirusBlokAda, initially spread via Microsoft Windows, and targeted Siemens industrial control systems.
"[30] In May 2011, the PBS program Need To Know cited a statement by Gary Samore, White House Coordinator for Arms Control and Weapons of Mass Destruction, in which he said, "we're glad they [the Iranians] are having trouble with their centrifuge machine and that we — the U.S. and its allies — are doing everything we can to make sure that we complicate matters for them," offering "winking acknowledgement" of United States involvement in Stuxnet.
[45] In the United Kingdom on 25 November 2010, Sky News reported that it had received information from an anonymous source at an unidentified IT security organization that Stuxnet, or a variation of the worm, had been traded on the black market.
[47][48] and commented that "the similar type of usage of both exploits together in different computer worms, at around the same time, indicates that the Equation Group and the Stuxnet developers are either the same or working closely together".
[49] In 2019, Chronicle researchers Juan Andres Guerrero-Saade and Silas Cutler presented evidence of at least four distinct threat actor malware platforms collaborating to create the different versions of Stuxnet.
[60] Unlike most malware, Stuxnet does little harm to computers and networks that do not meet specific configuration requirements; "The attackers took great care to make sure that only their designated targets were hit ...
[38] For its targets, Stuxnet contains, among other things, code for a man-in-the-middle attack that fakes industrial process control sensor signals so an infected system does not shut down due to detected abnormal behavior.
[64] The worm then uses other exploits and techniques such as peer-to-peer remote procedure call (RPC) to infect and update other computers inside private networks that are not directly connected to the Internet.
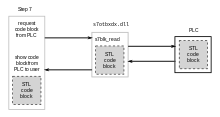
[67][38] According to researcher Ralph Langner,[72][73] once installed on a Windows system, Stuxnet infects project files belonging to Siemens' WinCC/PCS 7 SCADA control software[74] (Step 7), and subverts a key communication library of WinCC called s7otbxdx.dll.
Siemens recommends contacting customer support if an infection is detected and advises installing Microsoft updates for security vulnerabilities and prohibiting the use of third-party USB flash drives.
[92] In January 2024, de Volkskrant reported that Dutch engineer Erik van Sabben was the saboteur who had infiltrated the underground nuclear complex in the city of Natanz and installed equipment infected with Stuxnet.
[93] Ralph Langner, the researcher who identified that Stuxnet infected PLCs,[21] first speculated publicly in September 2010 that the malware was of Israeli origin, and that it targeted Iranian nuclear facilities.
[38] According to the Israeli newspaper Haaretz, in September 2010 experts on Iran and computer security specialists were increasingly convinced that Stuxnet was meant "to sabotage the uranium enrichment facility at Natanz – where the centrifuge operational capacity had dropped over the past year by 30 percent.
[101] A "serious nuclear accident" (supposedly the shutdown of some of its centrifuges[102]) occurred at the site in the first half of 2009, which is speculated to have forced Gholam Reza Aghazadeh, the head of the Atomic Energy Organization of Iran (AEOI), to resign.
[103] Statistics published by the Federation of American Scientists (FAS) show that the number of enrichment centrifuges operational in Iran mysteriously declined from about 4,700 to about 3,900 beginning around the time the nuclear incident WikiLeaks mentioned would have occurred.
[104] The Institute for Science and International Security (ISIS) suggests, in a report published in December 2010, that Stuxnet is a reasonable explanation for the apparent damage[105] at Natanz, and may have destroyed up to 1,000 centrifuges (10 percent) sometime between November 2009 and late January 2010.
But if the goal was to destroy a more limited number of centrifuges and set back Iran's progress in operating the FEP, while making detection difficult, it may have succeeded, at least temporarily.
[105]The Institute for Science and International Security (ISIS) report further notes that Iranian authorities have attempted to conceal the breakdown by installing new centrifuges on a large scale.
[107] According to The Washington Post, International Atomic Energy Agency (IAEA) cameras installed in the Natanz facility recorded the sudden dismantling and removal of approximately 900–1,000 centrifuges during the time the Stuxnet worm was reportedly active at the plant.
[108] On 15 February 2011, the Institute for Science and International Security released a report concluding that: Assuming Iran exercises caution, Stuxnet is unlikely to destroy more centrifuges at the Natanz plant.
[109]The Associated Press reported that the semi-official Iranian Students News Agency released a statement on 24 September 2010 stating that experts from the Atomic Energy Organization of Iran met in the previous week to discuss how Stuxnet could be removed from their systems.
[38] Israel, through Unit 8200,[125][126] has been speculated to be the country behind Stuxnet in many media reports[89][102][127] and by experts such as Richard A. Falkenrath, former Senior Director for Policy and Plans within the US Office of Homeland Security.
[67][140][141] Another date that appears in the code is "24 September 2007", the day that Iran's president Mahmoud Ahmadinejad spoke at Columbia University and made comments questioning the validity of the Holocaust.
[145] An article in The New York Times in January 2009 credited a then-unspecified program with preventing an Israeli military attack on Iran where some of the efforts focused on ways to destabilize the centrifuges.
Bumgarner pointed out that the centrifuges used to process fuel for nuclear weapons are a key target for cybertage operations and that they can be made to destroy themselves by manipulating their rotational speeds.
In the same report, Sean McGurk, a former cybersecurity official at the Department of Homeland Security noted that the Stuxnet source code could now be downloaded online and modified to be directed at new target systems.
This malware was capable of spreading only by being physically installed, probably by previously contaminated field equipment used by contractors working on Siemens control systems within the complex.
[164][165] Symantec, based on this report, continued the analysis of the threat, calling it "nearly identical to Stuxnet, but with a completely different purpose", and published a detailed technical paper.