Wireless LAN
Wireless LANs based on the IEEE 802.11 standards are the most widely used computer networks in the world.
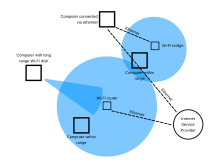
Hotspots provided by routers at restaurants, coffee shops, hotels, libraries, and airports allow consumers to access the internet with portable wireless devices.
Norman Abramson, a professor at the University of Hawaii, developed the world's first wireless computer communication network, ALOHAnet.
Early development included industry-specific solutions and proprietary protocols, but at the end of the 1990s these were replaced by technical standards, primarily the various versions of IEEE 802.11 (in products using the Wi-Fi brand name).
This allows data communications to avoid the crowded 2.4 GHz band, which is also shared with Bluetooth devices and microwave ovens.
A HomeRF group formed in 1997 to promote a technology aimed at residential use, but it disbanded in January 2003.
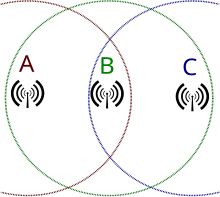
An independent BSS (IBSS) is an ad hoc network that contains no access points, which means they cannot connect to any other basic service set.
A distribution system (DS) connects access points in an extended service set.
Since wireless communication uses a more open medium for communication in comparison to wired LANs, the 802.11 designers also included encryption mechanisms: Wired Equivalent Privacy (WEP), no longer considered secure, Wi-Fi Protected Access (WPA, WPA2, WPA3), to secure wireless computer networks.
Many access points will also offer Wi-Fi Protected Setup, a quick, but no longer considered secure, method of joining a new device to an encrypted network.
In infrastructure mode, wireless clients, such as laptops and smartphones, connect to the WAP to join the network.
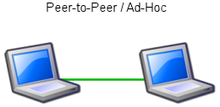
[4] In a peer-to-peer network wireless devices within range of each other can discover and communicate directly without involving central access points.
It allows a wireless network to be expanded using multiple access points without the need for a wired backbone to link them, as is traditionally required.
The notable advantage of a WDS over some other solutions is that it preserves the MAC addresses of client packets across links between access points.
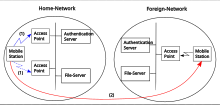
There are two definitions for wireless LAN roaming: WLAN signals often extends beyond the boundaries of a building and can create coverage where it is unwanted, offering a channel through which non-residents or other unauthorized people could compromise a system and retrieve personal data.
To prevent this it is usually sufficient to enforce the use of authentication, encryption, or VPN that requires a password for network connectivity.