Wi-Fi
Common obstructions, such as walls, pillars, home appliances, etc., may greatly reduce range, but this also helps minimize interference between different networks in crowded environments.
Hotspot coverage can be as small as a single room with walls that block radio waves or as large as many square kilometers using multiple overlapping access points with roaming permitted between them.
[18] This was in collaboration with the same group that helped create the standard: Vic Hayes, Bruce Tuch, Cees Links, Rich McGinn, and others from Lucent.
Certification may optionally include tests of IEEE 802.11 draft standards, interaction with cellular-phone technology in converged devices, and features relating to security set-up, multimedia, and power-saving.
A number of smartphones have a built-in mobile hotspot capability of this sort, though carriers often disable the feature, or charge a separate fee to enable it.
The city government plans to implement more than seven thousand kiosks over time, eventually making LinkNYC the largest and fastest public, government-operated Wi-Fi network in the world.
[69] Officials in South Korea's capital Seoul were moving to provide free Internet access at more than 10,000 locations around the city, including outdoor public spaces, major streets, and densely populated residential areas.
[80][81] The Wi-Fi RTT capability introduced in IEEE 802.11mc allows for positioning based on round trip time measurement, an improvement over the RSSI method.
With CSMA/CA stations attempt to avoid collisions by beginning transmission only after the channel is sensed to be idle,[90][91] but then transmit their packet data in its entirety.
In this frequency band, equipment may occasionally suffer interference from microwave ovens,[10] cordless telephones, USB 3.0 hubs,[95] Bluetooth and other devices.
[96] Spectrum assignments and operational limitations are not consistent worldwide: Australia and Europe allow for an additional two channels (12, 13) beyond the 11 permitted in the United States for the 2.4 GHz band, while Japan has three more (12–14).
[98] Wi-Fi's MAC and physical layer (PHY) specifications are defined by IEEE 802.11 for modulating and receiving one or more carrier waves to transmit the data in the infrared, and 2.4, 3.6, 5, 6, or 60 GHz frequency bands.
While each amendment is officially revoked when incorporated in the latest version of the standard, the corporate world tends to market to the revisions because they concisely denote capabilities of their products.
The success was recorded in Mobile Computing magazine (1999)[102] and later published formally in IEEE Transactions on Wireless Communications, 2002[103] and ACM SIGMETRICS Performance Evaluation Review, 2001.
Multiple antennas enable the equipment to exploit multipath propagation on the same frequency bands giving much higher speeds and longer range.
This standard uses several signal processing techniques such as multi-user MIMO and 4X4 Spatial Multiplexing streams, and wide channel bandwidth (160 MHz) to achieve its gigabit throughput.
[115] This effect does not apply equally to long-range Wi-Fi, since longer links typically operate from towers that transmit above the surrounding foliage.
Distance records (using non-standard devices) include 382 km (237 mi) in June 2007, held by Ermanno Pietrosemoli and EsLaRed of Venezuela, transferring about 3 MB of data between the mountain-tops of El Águila and Platillon.
[116][117] The Swedish National Space Agency transferred data 420 km (260 mi), using 6 watt amplifiers to reach an overhead stratospheric balloon.
These issues can become a problem in high-density areas, such as large apartment complexes or office buildings with multiple Wi-Fi access points.
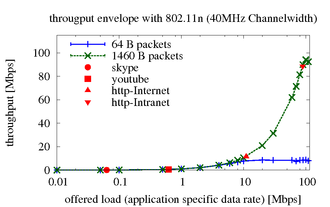
Due to the difference in the frame (header) lengths of these two media, the packet size of an application determines the speed of the data transfer.
This means that an application that uses small packets (e.g. VoIP) creates a data flow with high overhead traffic (low goodput).
These adapters connect to devices using various external or internal interconnects such as mini PCIe (mPCIe, M.2), USB, ExpressCard and previously PCI, Cardbus, and PC Card.
The security standard, Wi-Fi Protected Setup, allows embedded devices with a limited graphical user interface to connect to the Internet with ease.
[130] Increasingly in the last few years (particularly as of 2007[update]), embedded Wi-Fi modules have become available that incorporate a real-time operating system and provide a simple means of wirelessly enabling any device that can communicate via a serial port.
[150] Piggybacking often occurs unintentionally – a technically unfamiliar user might not change the default "unsecured" settings to their access point and operating systems can be configured to connect automatically to any available wireless network.
A user who happens to start up a laptop in the vicinity of an access point may find the computer has joined the network without any visible indication.
In combination with automatic discovery of other network resources (see DHCP and Zeroconf) this could lead wireless users to send sensitive data to the wrong middle-man when seeking a destination (see man-in-the-middle attack).
On an unsecured access point, an unauthorized user can obtain security information (factory preset passphrase or Wi-Fi Protected Setup PIN) from a label on a wireless access point and use this information (or connect by the Wi-Fi Protected Setup pushbutton method) to commit unauthorized or unlawful activities.
The United Kingdom's Health Protection Agency reported in 2007 that exposure to Wi-Fi for a year results in the "same amount of radiation from a 20-minute mobile phone call".