Advanced Access Content System
The standard has been adopted as the access restriction scheme for HD DVD and Blu-ray Disc (BD).
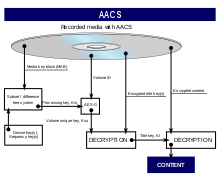
The principal difference between AACS and CSS (the DRM system used on DVDs) lies in how the device decryption keys and codes are organized.
The approach of AACS provisions each individual player with a unique set of decryption keys which are used in a broadcast encryption scheme.
[1][2] Volume IDs are unique identifiers or serial numbers that are stored on pre-recorded discs with special hardware.
The point of this is to prevent simple bit-by-bit copies, since the Volume ID is required (though not sufficient) for decoding content.
[3] To read the Volume ID, a cryptographic certificate (the Private Host Key) signed by the AACS LA is required.
This is set by a flag called the Image Constraint Token (ICT), which restricts the resolution for analog outputs to 960×540.
The German magazine "Der Spiegel" has reported about an unofficial agreement between film studios and electronics manufacturers to not use ICT until 2010 – 2012.
[9] On 5 June 2009, the licensing agreements for AACS were finalized, which were updated to make Cinavia detection on commercial Blu-ray disc players a requirement.
The Blu-ray standards adopted Mandatory Managed Copy later than HD DVD, after HP requested it.
On 24 February 2001, Dalit Naor, Moni Naor and Jeff Lotspiech published a paper entitled "Revocation and Tracing Schemes for Stateless Receivers", where they described a broadcast encryption scheme using a construct called Naor-Naor-Lotspiech subset-difference trees.
[15] With DeCSS in hindsight, the IEEE Spectrum magazine's readers voted AACS to be one of the technologies most likely to fail in the January 2005 issue.
[28] The processing key was widely published on the Internet after it was found and the AACS LA sent multiple DMCA takedown notices in the aim of censoring it.
[32] The AACS key extractions highlight the inherent weakness in any DRM system that permit software players for PCs to be used for playback of content.
No matter how many layers of encryption are employed, it does not offer any true protection, since the keys needed to obtain the unencrypted content stream must be available somewhere in memory for playback to be possible.
Apparently this program works even with movies released after the AACS LA expired the first batch of keys.
[37] While great care has been taken with AACS to ensure that contents are encrypted right up to the display device, on the first versions of some Blu-ray and HD DVD software players a perfect copy of any still frame from a film could be made simply by utilizing the Print Screen function of the Windows operating system.
[38][39] On 30 May 2007, Canadian encryption vendor Certicom sued Sony alleging that AACS violated two of its patents, "Strengthened public key protocol"[40] and "Digital signatures on a Smartcard.