CBC-MAC
In cryptography, a cipher block chaining message authentication code (CBC-MAC) is a technique for constructing a message authentication code (MAC) from a block cipher.
This interdependence ensures that a change to any of the plaintext bits will cause the final encrypted block to change in a way that cannot be predicted or counteracted without knowing the key to the block cipher.
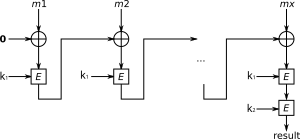
To calculate the CBC-MAC of message m, one encrypts m in CBC mode with zero initialization vector and keeps the last block.
The following figure sketches the computation of the CBC-MAC of a message comprising blocks
using a secret key k and a block cipher E: CBC-MAC on its own is not secure for variable-length messages[1] (see the discussion below) and is currently used to construct a pseudorandom function family[2] and as a component of the CCM mode.
The CBC-MAC construct is used as part of the CCM mode utilized in IEEE 802.11i and NIST SP 800-97 (as CCMP, the CCM encryption protocol for WPA2), IPsec,[3] and TLS 1.2,[4] as well as Bluetooth Low Energy (as of Bluetooth 4.0, see NIST SP 800-121 Rev2).
randomness extractor,[2] a method to generate bitstrings with full entropy) in NIST SP 800-90B.
FIPS PUB 113 Computer Data Authentication is a (now obsolete) U.S. government standard that specified the CBC-MAC algorithm using DES as the block cipher.
This is because an attacker who knows the correct authentication tag (i.e. CBC-MAC) pairs for two messages
we will perform an exclusive OR operation with the value derived for the MAC of the first message.
[8] There are three main ways of modifying CBC-MAC so that it is secure for variable length messages: 1) Input-length key separation; 2) Length-prepending; 3) Encrypt last block.
[8] In such a case, it may also be recommended to use a different mode of operation, for example, CMAC or HMAC to protect the integrity of variable-length messages.
One solution is to include the length of the message in the first block;[9] in fact CBC-MAC has been proven secure as long as no two messages that are prefixes of each other are ever used and prepending the length is a special case of this.
[12] One common mistake is to reuse the same key k for CBC encryption and CBC-MAC.
Although a reuse of a key for different purposes is a bad practice in general, in this particular case the mistake leads to a spectacular attack: Suppose Alice has sent to Bob the cipher text blocks
The tampered message, delivered to Bob in replacement of Alice's original, is
Bob first decrypts the message received using the shared secret key K to obtain corresponding plain text.
is produced when chaining the previous cipher text block into the exclusive-OR after decryption of
It follows that Bob will now compute the authentication tag using CBC-MAC over all the values of plain text which he decoded.
, we cannot "undo" the decryption process in the forward step of the computation of the message authentication code so as to produce the same tag; each modified
This example also shows that a CBC-MAC cannot be used as a collision-resistant one-way function: given a key it is trivial to create a different message which "hashes" to the same tag.
When encrypting data using a block cipher in cipher block chaining (or another) mode, it is common to introduce an initialization vector to the first stage of the encryption process.
It is typically required that this vector be chosen randomly (a nonce) and that it is not repeated for any given secret key under which the block cipher operates.
This provides semantic security, by means of ensuring the same plain text is not encrypted to the same cipher text, allowing an attacker to infer a relationship exists.
If we allow the initialization vector to be selected arbitrarily, it follows that the first block of plain text can potentially be modified (transmitting a different message) while producing the same message tag.
In particular, when computing the message tag for CBC-MAC, suppose we choose an initialization vector
As bits in both the plain text and initialization vector have been flipped in the same places, the modification is cancelled in this first stage, meaning the input to the block cipher is identical to that for
If no further changes are made to the plain text, the same tag will be derived despite a different message being transmitted.
However, if the attacker can predict what IV will be used for MAC verification, he or she can replay previously observed message by modifying the first data block to compensate for the change in the IV that will be used for the verification.
Another solution (in case protection against message replay attacks is not required) is to always use a zero vector IV.