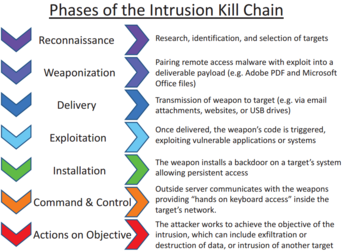
Cyber kill chain
[2] Lockheed Martin adapted the concept of the kill chain from a military setting to information security, using it as a method for modeling intrusions on a computer network.
Since then, the "cyber kill chain" has been adopted by data security organizations to define phases of cyberattacks.
[7] A cyber kill chain reveals the phases of a cyberattack: from early reconnaissance to the goal of data exfiltration.
[12] Others have noted that the traditional cyber kill chain isn't suitable to model the insider threat.
The unified model can be used to analyze, compare, and defend against end-to-end cyberattacks by advanced persistent threats (APTs).