Electronic signature
The USA's E-Sign Act,[7][8] signed June 30, 2000 by President Clinton was described months later as "more like a seal than a signature.
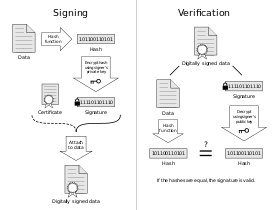
"[9] An electronic signature is intended to provide a secure and accurate identification method for the signatory during a transaction.
[13] Since well before the American Civil War began in 1861, morse code was used to send messages electrically via the telegraph.
An early acceptance of the enforceability of telegraphic messages as electronic signatures came from a New Hampshire Supreme Court case, Howley v. Whipple, in 1869.
[14][15] In the 1980s, many companies and even some individuals began using fax machines for high-priority or time-sensitive delivery of documents.
[16] Courts in various jurisdictions have decided that enforceable legality of electronic signatures can include agreements made by email, entering a personal identification number (PIN) into a bank ATM, signing a credit or debit slip with a digital pen pad device (an application of graphics tablet technology) at a point of sale, installing software with a clickwrap software license agreement on the package, and signing electronic documents online.
In the United States, the definition of what qualifies as an electronic signature is wide and is set out in the Uniform Electronic Transactions Act ("UETA") released by the National Conference of Commissioners on Uniform State Laws (NCCUSL) in 1999.
[27] It was influenced by ABA committee white papers and the uniform law promulgated by NCCUSL.
[28] Only New York and Illinois have not enacted UETA,[28] but each of those states has adopted its own electronic signatures statute.
[32] In Australia, an electronic signature is recognised as "not necessarily the writing in of a name, but maybe any mark which identifies it as the act of the party.” [33] Under the Electronic Transactions Acts in each Federal, State and Territory jurisdiction, an electronic signature may be considered enforceable if (a) there was a method used to identify the person and to indicate that person’s intention in respect of the information communicated and the method was either: (i) as reliable as appropriate for the purpose for which the electronic communication was generated or communicated, in light of all the circumstances, including the relevant agreement; or (ii) proven in fact to have fulfilled the functions above by itself or together with further evidence and the person to whom the signature is required to be given consents to that method.
Biometric measurements of this type are useless as passwords because they can't be changed if compromised.
For example, a replay of the electronic signal produced and submitted to the computer system responsible for 'affixing' a signature to a document can be collected via wiretapping techniques.
[citation needed] Many commercially available fingerprint sensors have low resolution and can be deceived with inexpensive household items (for example, gummy bear candy gel).