Encrypted key exchange
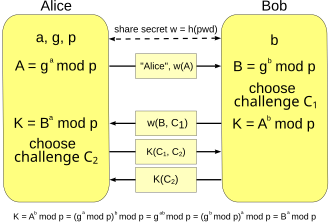
[1] Although several of the forms of EKE in this paper were later found to be flawed [clarification needed], the surviving, refined, and enhanced forms of EKE effectively make this the first method to amplify a shared password into a shared key, where the shared key may subsequently be used to provide a zero-knowledge password proof or other functions.
A second paper describes Augmented-EKE,[2] and introduced the concept of augmented password-authenticated key agreement for client/server scenarios.
A version of EKE based on Diffie–Hellman, known as DH-EKE, has survived attack and has led to improved variations, such as the PAK family of methods in IEEE P1363.2.
U.S. patent 5,241,599, owned by Lucent, describes the initial EKE method.
U.S. patent 5,440,635, owned by Lucent, describes the augmented EKE method.