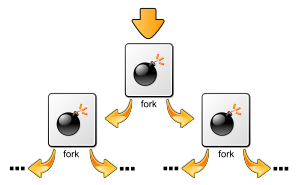
Fork bomb
In computing, a fork bomb (also called rabbit virus) is a denial-of-service (DoS) attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation.
It may have descended from a similar attack called RABBITS reported from 1969 on a Burroughs 5500 at the University of Washington.
[2][3] A basic implementation of a fork bomb is an infinite loop that repeatedly launches new copies of itself.
[9] As a fork bomb's mode of operation is entirely encapsulated by creating new processes, one way of preventing a fork bomb from severely affecting the entire system is to limit the maximum number of processes that a single user may own.
[12] Modern Linux systems also allow finer-grained fork bomb prevention through cgroups and process number (PID) controllers.