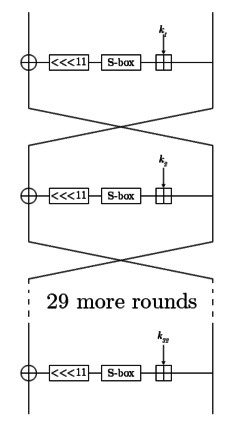
GOST (block cipher)
GOST 28147 was a Soviet alternative to the United States standard algorithm, DES.
Its S-boxes can be secret, and they contain about 354 (log2(16!8)) bits of secret information, so the effective key size can be increased to 610 bits; however, a chosen-key attack can recover the contents of the S-boxes in approximately 232 encryptions.
This led to speculation that organizations the government wished to spy on were given weak S-boxes.
[2] The latest cryptanalysis of GOST shows that it is secure in a theoretical sense.
Since 2007, several attacks have been developed against reduced-round GOST implementations and/or weak keys.
[12] Isobe had already published a single key attack on the full GOST cipher,[13] which Dinur, Dunkelman, and Shamir improved upon, reaching 2224 time complexity for 232 data and 236 memory, and 2192 time complexity for 264 data.
[14] Since the attacks reduce the expected strength from 2256 (key length) to around 2178, the cipher can be considered broken.