IT risk
Various events or incidents that compromise IT in some way can therefore cause adverse impacts on the organization's business processes or mission, ranging from inconsequential to catastrophic in scale.
[2] Alternative methods of measuring IT risk typically involve assessing other contributory factors such as the threats, vulnerabilities, exposures, and asset values.
Front line IT departments and NOC's tend to measure more discrete, individual risks.
When measuring risk of any kind, selecting the correct equation for a given threat, asset, and available data is an important step.
You have internal knowledge of and a fair amount of control over assets, which are tangible and intangible things that have value.
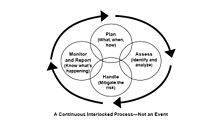
[17]The field of IT risk management has spawned a number of terms and techniques which are unique to the industry.
So R can be function of four factors: If numerical values (money for impact and probabilities for the other factors), the risk can be expressed in monetary terms and compared to the cost of countermeasures and the residual risk after applying the security control.
The continuous update and maintenance of an ISMS is in turn part of an organisation's systematic approach for identifying, assessing, and managing information security risks.
[24]The Certified Information Systems Auditor Review Manual 2006 by ISACA provides this definition of risk management: "Risk management is the process of identifying vulnerabilities and threats to the information resources used by an organization in achieving business objectives, and deciding what countermeasures, if any, to take in reducing risk to an acceptable level, based on the value of the information resource to the organization.
"[32] New York's SHIELD Act requires that organizations that manage NY residents' information “develop, implement and maintain reasonable safeguards to protect the security, confidentiality and integrity of the private information including, but not limited to, disposal of data.” This concept will influence how businesses manage their risk management plan as compliance requirements develop.