Address Resolution Protocol
ARP has been implemented with many combinations of network and data link layer technologies, such as IPv4, Chaosnet, DECnet and Xerox PARC Universal Packet (PUP) using IEEE 802 standards, FDDI, X.25, Frame Relay and Asynchronous Transfer Mode (ATM).
The packets are carried at the data link layer of the underlying network as raw payload.
The message header specifies the types of network in use at each layer as well as the size of addresses of each.
ARP parameter values have been standardized and are maintained by the Internet Assigned Numbers Authority (IANA).
ARP's placement within the Internet protocol suite and the OSI model may be a matter of confusion or even of dispute.
[6] Two computers, A and B, are connected to the same local area network with no intervening gateway or router.
All nodes of the network receive the message, but only B replies since it has the requested IP address.
Typically, network nodes maintain a lookup cache that associates IP and MAC addressees.
When several such probes have been sent, with slight delays, and none receive replies, it can reasonably be expected that no conflict exists.
An alternative way is to broadcast an ARP reply with the sender's SHA and SPA duplicated in the target fields (TPA=SPA, THA=SHA).
ARP announcements are also used by some network interfaces to provide load balancing for incoming traffic.
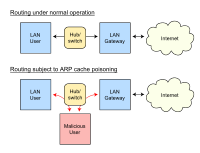
[15] This function can be dangerous from a cybersecurity viewpoint since an attacker can obtain information about the other hosts of its subnet to save in their ARP cache (ARP spoofing) an entry where the attacker MAC is associated, for instance, to the IP of the default gateway, thus allowing them to intercept all the traffic to external networks.
ARP mediation refers to the process of resolving Layer-2 addresses through a virtual private wire service (VPWS) when different resolution protocols are used on the connected circuits, e.g., Ethernet on one end and Frame Relay on the other.
RARP is obsolete; it was replaced by BOOTP, which was later superseded by the Dynamic Host Configuration Protocol (DHCP).
This data is maintained primarily by interpreting ARP packets from the local network link.
Since at least the 1980s,[20] networked computers have a utility called arp for interrogating or manipulating this database.