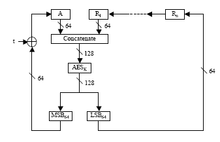
Key wrap
The constructions are typically built from standard primitives such as block ciphers and cryptographic hash functions.
The resulting algorithms would be formally evaluated by NIST, and eventually approved for use in NIST-certified cryptographic modules.
Based on the resulting algorithms, the design requirements appear to be (1) confidentiality, (2) integrity protection (authentication), (3) efficiency, (4) use of standard (approved) underlying primitives such as the Advanced Encryption Standard (AES) and the Secure Hash Algorithm (SHA-1), and (5) consideration of additional circumstances (e.g., resilience to operator error, low-quality random number generators).
AESKW, TDKW and AKW2 also provide the ability to authenticate cleartext "header", an associated block of data that is not encrypted.
Among their general findings, they noted the lack of clearly stated design goals for the algorithms, and the absence of security proofs for all constructions.