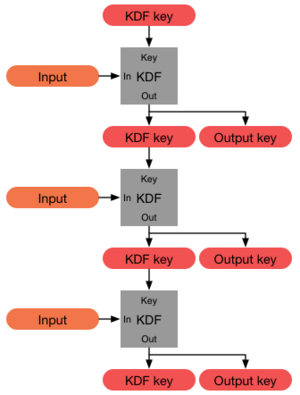
Key derivation function
[citation needed] Although high throughput is a desirable property in general-purpose hash functions, the opposite is true in password security applications in which defending against brute-force cracking is a primary concern.
Although bcrypt was employed to protect the hashes (making large scale brute-force cracking expensive and time-consuming), a significant portion of the accounts in the compromised data also contained a password hash based on the fast general-purpose MD5 algorithm, which made it possible for over 11 million of the passwords to be cracked in a matter of weeks.
Modern password-based key derivation functions, such as PBKDF2,[2] are based on a recognized cryptographic hash, such as SHA-2, use more salt (at least 64 bits and chosen randomly) and a high iteration count.
The values of the salt and the number of iterations (if it is not fixed) are stored with the hashed password or sent as cleartext (unencrypted) with an encrypted message.
A practical limit on the iteration count is the unwillingness of users to tolerate a perceptible delay in logging into a computer or seeing a decrypted message.
Password hash functions should be relatively expensive to calculate in case of brute-force attacks, and the key stretching of KDFs happen to provide this characteristic.
[14] As of May 2023, the Open Worldwide Application Security Project (OWASP) recommends the following KDFs for password hashing, listed in order of priority:[15]