Network topology
A wide variety of physical topologies have been used in LANs, including ring, bus, mesh and star.
Conversely, mapping the data flow between the components determines the logical topology of the network.
Physically, Avionics Full-Duplex Switched Ethernet (AFDX) can be a cascaded star topology of multiple dual redundant Ethernet switches; however, the AFDX virtual links are modeled as time-switched single-transmitter bus connections, thus following the safety model of a single-transmitter bus topology previously used in aircraft.
Logical topologies are often closely associated with media access control methods and protocols.
The transmission media (often referred to in the literature as the physical media) used to link devices to form a computer network include electrical cables (Ethernet, HomePNA, power line communication, G.hn), optical fiber (fiber-optic communication), and radio waves (wireless networking).
A widely adopted family of transmission media used in local area network (LAN) technology is collectively known as Ethernet.
The media and protocol standards that enable communication between networked devices over Ethernet are defined by IEEE 802.3.
Wireless LAN standards (e.g. those defined by IEEE 802.11) use radio waves, or others use infrared signals as a transmission medium.
Wireless options command a price premium that can make purchasing wired computers, printers and other devices a financial benefit.
Before making the decision to purchase hard-wired technology products, a review of the restrictions and limitations of the selections is necessary.
In the simplest of serial arrangements, one RS-232 transmitter can be connected by a pair of wires to one receiver, forming two nodes on one link, or a Point-to-Point topology.
For example, the NIC may have a connector for accepting a cable, or an aerial for wireless transmission and reception, and the associated circuitry.
A repeater is an electronic device that receives a network signal, cleans it of unnecessary noise and regenerates it.
[15] In most twisted pair Ethernet configurations, repeaters are required for cable that runs longer than 100 meters.
Multi-layer switches are capable of routing based on layer 3 addressing or additional logical levels.
Firewalls are typically configured to reject access requests from unrecognized sources while allowing actions from recognized ones.
The vital role firewalls play in network security grows in parallel with the constant increase in cyber attacks.
Using circuit-switching or packet-switching technologies, a point-to-point circuit can be set up dynamically and dropped when no longer needed.
The value of an on-demand point-to-point connection is proportional to the number of potential pairs of subscribers and has been expressed as Metcalfe's Law.
If a message is intended for a computer partway down the line, each system bounces it along in sequence until it reaches the destination.
In local area networks using bus topology, each node is connected by interface connectors to a single central cable.
In a distributed bus network, all of the nodes of the network are connected to a common transmission medium with more than two endpoints, created by adding branches to the main section of the transmission medium – the physical distributed bus topology functions in exactly the same fashion as the physical linear bus topology because all nodes share a common transmission medium.
All traffic that traverses the network passes through the central hub, which acts as a signal repeater.
The primary disadvantage of the star topology is that the hub represents a single point of failure.
Repeaters allow greater transmission distance, further than would be possible using just the transmitting power of the central node.
[20] The star topology reduces the probability of a network failure by connecting all of the peripheral nodes (computers, etc.)
These network switches will learn the layout of the network by listening on each port during normal data transmission, examining the data packets and recording the address/identifier of each connected node and which port it is connected to in a lookup table held in memory.
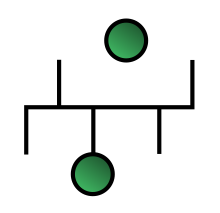
Daisy chain topology is a way of connecting network nodes in a linear or ring structure.
Decentralization is often used to compensate for the single-point-failure disadvantage that is present when using a single device as a central node (e.g., in star and tree networks).
This is similar in some ways to a grid network, where a linear or ring topology is used to connect systems in multiple directions.