Proof of work
[2][3] The concept was adapted to digital tokens by Hal Finney in 2004 through the idea of "reusable proof of work" using the 160-bit secure hash algorithm 1 (SHA-1).
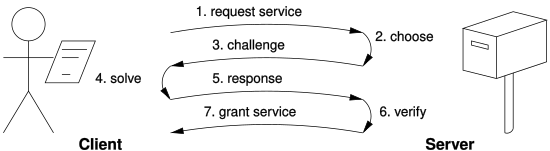
[5] A key feature of proof-of-work schemes is their asymmetry: the work – the computation – must be moderately hard (yet feasible) on the prover or requester side but easy to check for the verifier or service provider.
[6][7] The purpose of proof-of-work algorithms is not proving that certain work was carried out or that a computational puzzle was "solved", but deterring manipulation of data by establishing large energy and hardware-control requirements to be able to do so.
[8] The concept of Proof of Work (PoW) has its roots in early research on combating spam and preventing denial-of-service attacks.
This task was trivial for legitimate users but would impose a significant cost on spammers attempting to send bulk messages.
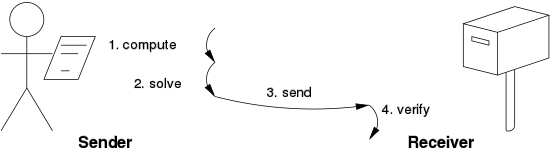
Hashcash's system was based on the concept of finding a hash value that met certain criteria, a task that required computational effort and thus served as a "proof of work."
One popular system, used in Hashcash, uses partial hash inversions to prove that computation was done, as a goodwill token to send an e-mail.
For instance, the following header represents about 252 hash computations to send a message to calvin@comics.net on January 19, 2038: It is verified with a single computation by checking that the SHA-1 hash of the stamp (omit the header name X-Hashcash: including the colon and any amount of whitespace following it up to the digit '1') begins with 52 binary zeros, that is 13 hexadecimal zeros:[1] Whether PoW systems can actually solve a particular denial-of-service issue such as the spam problem is subject to debate;[10][11] the system must make sending spam emails obtrusively unproductive for the spammer, but should also not prevent legitimate users from sending their messages.
Here is a list of known proof-of-work functions: At the IACR conference Crypto 2022 researchers presented a paper describing Ofelimos, a blockchain protocol with a consensus mechanism based on "proof of useful work" (PoUW).
Rather than miners consuming energy in solving complex, but essentially useless, puzzles to validate transactions, Ofelimos achieves consensus while simultaneously providing a decentralized optimization problem solver.
But in bitcoin, double-spend protection is provided by a decentralized P2P protocol for tracking transfers of coins, rather than the hardware trusted computing function used by RPoW.
[31] Some PoWs claim to be ASIC-resistant,[32] i.e. to limit the efficiency gain that an ASIC can have over commodity hardware, like a GPU, to be well under an order of magnitude.
[35] In November 2022 the state of New York enacted a two-year moratorium on cryptocurrency mining that does not completely use renewable energy as a power source for two years.