SHA-2
SHA-512/224 and SHA-512/256 are also truncated versions of SHA-512, but the initial values are generated using the method described in Federal Information Processing Standards (FIPS) PUB 180-4.
[1][2] With the publication of FIPS PUB 180-2, NIST added three additional hash functions in the SHA family.
The algorithms were first published in 2001 in the draft FIPS PUB 180-2, at which time public review and comments were accepted.
[4] In February 2004, a change notice was published for FIPS PUB 180-2, specifying an additional variant, SHA-224, defined to match the key length of two-key Triple DES.
The primary motivation for updating the standard was relocating security information about the hash algorithms and recommendations for their use to Special Publications 800-107 and 800-57.
[8][9][10] Detailed test data and example message digests were also removed from the standard, and provided as separate documents.
[12] In March 2012, the standard was updated in FIPS PUB 180-4, adding the hash functions SHA-512/224 and SHA-512/256, and describing a method for generating initial values for truncated versions of SHA-512.
The SHA-2 hash function is implemented in some widely used security applications and protocols, including TLS and SSL, PGP, SSH, S/MIME, and IPsec.
The inherent computational demand of SHA-2 algorithms has driven the proposal of more efficient solutions, such as those based on application-specific integrated circuits (ASICs) hardware accelerators.
The Google Chrome team announced a plan to make their web browser gradually stop honoring SHA-1-dependent TLS certificates over a period from late 2014 and early 2015.
[26][27][28] Similarly, Microsoft announced[29] that Internet Explorer and Edge [Legacy] would stop honoring public SHA-1-signed TLS certificates from February 2017.
Mozilla disabled SHA-1 in early January 2016, but had to re-enable it temporarily via a Firefox update, after problems with web-based user interfaces of some router models and security appliances.
There are practical circumstances in which this is possible; until the end of 2008, it was possible to create forged SSL certificates using an MD5 collision which would be accepted by widely used web browsers.
[31] Increased interest in cryptographic hash analysis during the SHA-3 competition produced several new attacks on the SHA-2 family, the best of which are given in the table below.
As of December 2013,[update] there are over 1300 validated implementations of SHA-256 and over 900 of SHA-512, with only 5 of them being capable of handling messages with a length in bits not a multiple of eight while supporting both variants.
Even a small change in the message will (with overwhelming probability) result in a different hash, due to the avalanche effect.
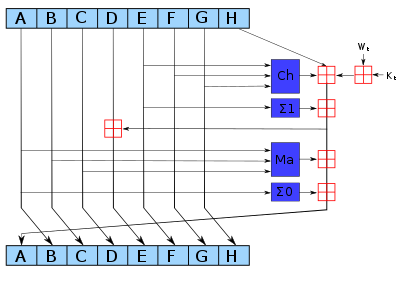
The bitwise rotation uses different constants for SHA-512. The given numbers are for SHA-256.
The red is addition modulo 2 32 for SHA-256, or 2 64 for SHA-512.




