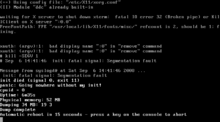
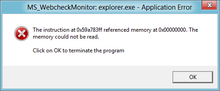
Segmentation fault
Segmentation faults are a common class of error in programs written in languages like C that provide low-level memory access and few to no safety checks.
Many programming languages have mechanisms designed to avoid segmentation faults and improve memory safety.
[3] Other languages, such as Lisp and Java, employ garbage collection,[4] which avoids certain classes of memory errors that could lead to segmentation faults.
On Unix-like operating systems, a signal called SIGSEGV (abbreviated from segmentation violation) is sent to the offending process.
Determining the root cause – debugging the bug – can be simple in some cases, where the program will consistently cause a segmentation fault (e.g., dereferencing a null pointer), while in other cases the bug can be difficult to reproduce and depend on memory allocation on each run (e.g., dereferencing a dangling pointer).
For example, Linux systems using the grsecurity patch may log SIGSEGV signals in order to monitor for possible intrusion attempts using buffer overflows.
[7] Depending on the architecture and operating system, the running program can not only handle the event but may extract some information about its state like getting a stack trace, processor register values, the line of the source code when it was triggered, memory address that was invalidly accessed[8] and whether the action was a read or a write.
In this case, when the system allows, it is possible to handle the event and increment the processor program counter to "jump" over the failing instruction to continue the execution.
Compiling such a program with a compiler that does not check for the assignment of read-only locations at compile time, and running it on a Unix-like operating system produces the following runtime error: Backtrace of the core file from GDB: This code can be corrected by using an array instead of a character pointer, as this allocates memory on stack and initializes it to the value of the string literal: Even though string literals should not be modified (this has undefined behavior in the C standard), in C they are of static char [] type,[11][12][13] so there is no implicit conversion in the original code (which points a char * at that array), while in C++ they are of static const char [] type, and thus there is an implicit conversion, so compilers will generally catch this particular error.
[14] Infinite recursion may not necessarily result in a stack overflow depending on the language, optimizations performed by the compiler and the exact structure of a code.
In this case, the behavior of unreachable code (the return statement) is undefined, so the compiler can eliminate it and use a tail call optimization that might result in no stack usage.
Other optimizations could include translating the recursion into iteration, which given the structure of the example function would result in the program running forever, while probably not overflowing its stack.