SYN flood
A SYN flood is a form of denial-of-service attack on data communications in which an attacker rapidly initiates a connection to a server without finalizing the connection.
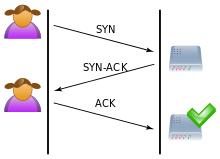
[3] When a client attempts to start a TCP connection to a server, the client and server exchange a series of messages which normally runs like this: This is called the TCP three-way handshake, and is the foundation for every connection established using the TCP protocol.
A SYN flood attack works by not responding to the server with the expected ACK code.
The server will wait for the acknowledgement for some time, as simple network congestion could also be the cause of the missing ACK.
There are a number of well-known countermeasures listed in RFC 4987 including: