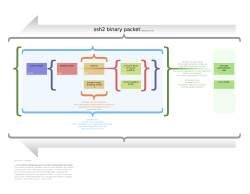
Secure Shell
SSH was designed for Unix-like operating systems as a replacement for Telnet and unsecured remote Unix shell protocols, such as the Berkeley Remote Shell (rsh) and the related rlogin and rexec protocols, which all use insecure, plaintext methods of authentication, like passwords.
In the simplest manner, both ends of a communication channel use automatically generated public-private key pairs to encrypt a network connection, and then use a password to authenticate the user.
On Unix-like systems, the list of authorized public keys is typically stored in the home directory of the user that is allowed to log in remotely, in the file ~/.ssh/authorized_keys.
The private key can also be looked for in standard places, and its full path can be specified as a command line setting (the option -i for ssh).
Both are commonly present on most modern operating systems, including macOS, most distributions of Linux, OpenBSD, FreeBSD, NetBSD, Solaris and OpenVMS.
File managers for UNIX-like systems (e.g. Konqueror) can use the FISH protocol to provide a split-pane GUI with drag-and-drop.
The open source Windows program WinSCP[6] provides similar file management (synchronization, copy, remote delete) capability using PuTTY as a back-end.
Both WinSCP[7] and PuTTY[8] are available packaged to run directly off a USB drive, without requiring installation on the client machine.
SSH is important in cloud computing to solve connectivity problems, avoiding the security issues of exposing a cloud-based virtual machine directly on the Internet.
[13] The goal of SSH was to replace the earlier rlogin, TELNET, FTP[14] and rsh protocols, which did not provide strong authentication nor guarantee confidentiality.
[17] In 2006, after being discussed in a working group named "secsh",[18] a revised version of the SSH protocol, SSH-2 was adopted as a standard.
For example, it introduces new key-exchange mechanisms like Diffie–Hellman key exchange, improved data integrity checking via message authentication codes like MD5 or SHA-1, which can be negotiated between client and server.
SSH-2 also adds stronger encryption methods like AES which eventually replaced weaker and compromised ciphers from the previous standard like 3-des.
[29] As of 2005[update], OpenSSH was the single most popular SSH implementation, being the default version in a large number of operating system distributions.
In 2023, an alternative to traditional SSH was proposed under the name SSH3[31][32][33] by PhD student François Michel and Professor Olivier Bonaventure and its code has been made open source.
Many of these updated implementations contained a new integer overflow vulnerability[45] that allowed attackers to execute arbitrary code with the privileges of the SSH daemon, typically root.
[47] Since SSH-1 has inherent design flaws which make it vulnerable, it is now generally considered obsolete and should be avoided by explicitly disabling fallback to SSH-1.
[49] On December 28, 2014 Der Spiegel published classified information[50] leaked by whistleblower Edward Snowden which suggests that the National Security Agency may be able to decrypt some SSH traffic.
[52][53] However, the risk is mitigated by the requirement to intercept a genuine ssh session, and that the attack is restricted in its scope, fortuitously resulting mostly in failed connections.