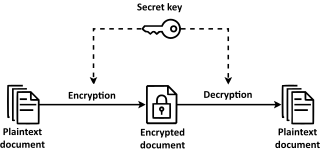
Symmetric-key algorithm
[1] The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link.
With exception of the one-time pad they have a smaller key size, which means less storage space and faster transmission.
Examples of popular symmetric-key algorithms include Twofish, Serpent, AES (Rijndael), Camellia, Salsa20, ChaCha20, Blowfish, CAST5, Kuznyechik, RC4, DES, 3DES, Skipjack, Safer, and IDEA.
[citation needed] It is also possible to increase the key length or the rounds in the encryption process to better protect against attack.
[13] Quantum computers would exponentially increase the speed at which these ciphers can be decoded; notably, Grover's algorithm would take the square-root of the time traditionally required for a brute-force attack, although these vulnerabilities can be compensated for by doubling key length.
[14] For example, a 128 bit AES cipher would not be secure against such an attack as it would reduce the time required to test all possible iterations from over 10 quintillion years to about six months.
All early cryptographic systems required either the sender or the recipient to somehow receive a copy of that secret key over a physically secure channel.
Nearly all modern cryptographic systems still use symmetric-key algorithms internally to encrypt the bulk of the messages, but they eliminate the need for a physically secure channel by using Diffie–Hellman key exchange or some other public-key protocol to securely come to agreement on a fresh new secret key for each session/conversation (forward secrecy).
However, lack of randomness in those generators or in their initialization vectors is disastrous and has led to cryptanalytic breaks in the past.