User story
They facilitate sensemaking and communication; and may help software teams document their understanding of the system and its context.
User stories can be developed through discussion with stakeholders, based on personas or are simply made up.
[15] Chris Matts suggested that "hunting the value" was the first step in successfully delivering software, and proposed this alternative:[16] Another template based on the Five Ws specifies:[17] A template that's commonly used to improve security is called the "Evil User Story" or "Abuse User Story" and is used as a way to think like a hacker in order to consider scenarios that might occur in a cyber-attack.
User stories are prioritized by the customer (or the product owner in Scrum) to indicate which are most important for the system and will be broken down into tasks and estimated by the developers.
[This quote needs a citation] Some may write the acceptance criteria in typical agile format, Given-When-Then.
However, user stories facilitate sensemaking without undue problem structuring, which is linked to success.
While some suggest to use 'epic' and 'theme' as labels for any thinkable kind of grouping of user stories, organization management tends to use it for strong structuring and uniting work loads.
In Jira, 'themes' exist (for tracking purposes) that allow to cross-relate and group items of different parts of the fixed hierarchy.
But another definition of themes is: a set of stories, epics, features etc for a user that forms a common semantic unit or goal.
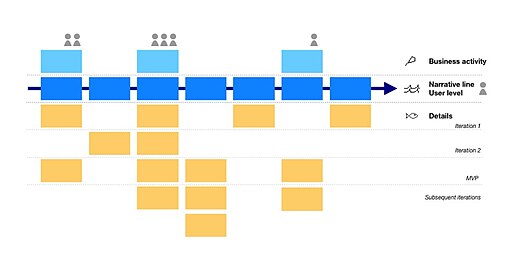
The technique was developed by Jeff Patton from 2005 to 2014 to address the risk of projects flooded with very detailed user stories that distract from realizing the product's main objectives.
The horizontal cross-cutting narrative line is then drawn by identifying the main tasks of the individual user involved in these business activities.
Its narrative line focuses on the chronology of phases and actions that a single user has to perform in order to achieve their objectives.
Kent Beck, Alistair Cockburn, Martin Fowler and others discussed this topic further on the c2.com wiki (the home of extreme programming).