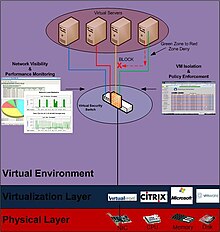
Virtual security switch
As a result, companies such as VMware created a resource called a virtual switch.
Because switches are layer 2 devices that create a single broadcast domain, virtual security switches alone cannot fully replicate the network segmentation and isolation typically employed in a multi-tiered physical network.
Because virtual machines are essentially operating systems and applications packaged into a single file (called disk images), they have now become more mobile.
No longer is it required for an administrator to go through the lengthy software installation process, because these virtual disk images have pre-installed operating systems and applications.
A Virtual Security Switch can isolate VM’s from each other, restrict what types of communication is allowed between each other as well as monitor for the spread of malicious content or denial of service attacks.
Since then, VMware, Cisco, Juniper and others have shipped virtual networking security products[which?]