Aircrack-ng
Aircrack-ng is a network software suite consisting of a detector, packet sniffer, WEP and WPA/WPA2-PSK cracker and analysis tool for 802.11 wireless LANs.
It works with any wireless network interface controller whose driver supports raw monitoring mode and can sniff 802.11a, 802.11b and 802.11g traffic.
[5] Its main goal was to recover 802.11 wireless networks WEP keys using an implementation of the Fluhrer, Mantin and Shamir (FMS) attack alongside the ones shared by a hacker named KoreK.
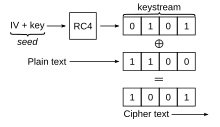
The output of RC4's pseudo random generation algorithm (PRGA) follows a XOR operation in combination with the plaintext, and produces the ciphertext.
[16] Since the IV values will eventually be reused and collide (given enough packets and time), WEP is vulnerable to statistical attacks.
In 2015, the Wi-Fi Alliance recommended in a technical note that network administrators should discourage the use of WPA and that vendors should remove support for it and rely instead on the newer WPA2 standard.
[26] Unlike WPA, WPA2-PSK uses the more secure Advanced Encryption Standard (AES) in CCM mode (Counter-Mode-CBC-MAC Protocol), instead of TKIP.
[15] In March 2000, a presentation by Dan Simon, Bernard Aboba, and Tim Moore of Microsoft provided a summary of 802.11 vulnerabilities.
[30] In addition, they wrote that because some implementations of WEP derive the key from a password, dictionary attacks are easier than pure brute force.
[31][17] In May 2001, William A. Arbaugh of the University of Maryland presented his inductive chosen-plaintext attack against WEP with the conclusion that the protocol is vulnerable to packet forgery.
[17] In August 2001, in the paper Weaknesses in the Key Scheduling Algorithm of RC4, authors Scott Fluhrer, Itsik Mantin, and Adi Shamir performed a cryptoanalysis of the KSA, citing Wagner among others.
[33][13] In 2004, a hacker using the pseudonym KoreK posted a series of attacks on the NetStumbler.org forum, which were incorporated into the original aircrack 1.2 by Christophe Devine.
[34][35] That same month, aircrack began supporting replay attacks against WEP, which use ARP requests to generate more IVs and make key recovery easier.
[37] The name of the attack derives from its inherent working: a packet is intercepted, "chops" off a part of it and sends a modified version to the Access Point, who will drop it if not valid.
Taking advantage of the fact that at least part of the plaintext of some packets may be known, and that the fragments may have the same IV, data can be injected at will, flooding the network to statistically increase the chances of recovering the key.
It decreased the number of initialization vectors or IVs needed to decrypt a WEP key and has been included in the aircrack-ng suite since the 0.9 release.
At this point, ARP packets are sent in the process of obtaining a local IP address, and airbase-ng can collect IVs that can later be used by aircrack-ng to recover the key.
[51] Monitor mode refers to a provision in the IEEE 802.11 standard for auditing and design purposes,[60] in which a wireless card can capture packets in air range.
wesside-ng is a proof of concept based on the tool wesside, originally written by Andrea Bittau to demonstrate his fragmentation attack.
[66] airolib-ng can create a database of pre-computed hash tables by computing the Pairwise Master Keys (PMK) captured during the 4-way handshaking process.
[68][6] During the 4-way handshaking process, the PMK is used, among other parameters, to generate a Pairwise Transient Key (PTK), which is used to encrypt data between the client and Access Point.
kstats is a tool for displaying the Fluhrer, Mantin and Shamir attack algorithm votes[note 1] for an IVS dump with a given WEP key.