MAC address
Within the Open Systems Interconnection (OSI) network model, MAC addresses are used in the medium access control protocol sublayer of the data link layer.
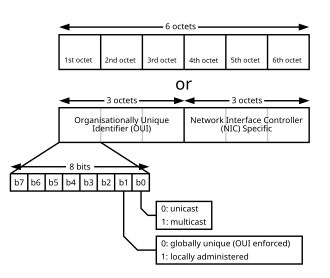
MAC addresses are formed according to the principles of two numbering spaces based on extended unique identifiers (EUIs) managed by the Institute of Electrical and Electronics Engineers (IEEE): EUI-48—which replaces the obsolete term MAC-48—and EUI-64.
In addition, the EUI-64 numbering system originally encompassed both MAC-48 and EUI-48 identifiers by a simple translation mechanism.
All other potential uses based on the OUI from which the IABs are allocated are reserved and remain the property of the IEEE Registration Authority.
[3] The remainder of the address (three octets in EUI-48 or five in EUI-64) are assigned by that organization in nearly any manner they please, subject to the constraint of uniqueness.
Each new virtual machine is started with a MAC address set by assigning the last three bytes to be unique on the local network.
A historical example of this hybrid situation is the DECnet protocol, where the universal MAC address (with Digital Equipment Corporation's OUI AA-00-04) is administered locally.
In a modern wired setting (i.e. with switches, not simple hubs) the collision domain usually is the length of the Ethernet cabling between two network interfaces.
If the least significant bit of the first octet is set to 1 (i.e. the second hexadecimal digit is odd) the frame will still be sent only once; however, network interface controllers will choose to accept or ignore it based on criteria other than the matching of their individual MAC addresses: for example, based on a configurable list of accepted multicast MAC addresses.
This additional partitioning is called Structured Local Address Plan (SLAP) and its usage is optional.
Common networked consumer devices such as PCs, smartphones and tablet computers use EUI-48 addresses.
On most Unix-like systems, the command utility ifconfig may be used to remove and add link address aliases.
[18] Hence, various configuration scripts and utilities permit the randomization of the MAC address at the time of booting or before establishing a network connection.
Some modern operating systems, such as Apple iOS and Android, especially in mobile devices, are designed to assign a random MAC address to their network interface when scanning for wireless access points to avert tracking systems.
According to Edward Snowden, the US National Security Agency has a system that tracks the movements of mobile devices in a city by monitoring MAC addresses.
[21] To avert this practice, Apple started using random MAC addresses in iOS devices while scanning for networks.
MAC address randomization during scanning was added in Android starting from version 6.0,[20] in Windows 10,[22] and in Linux 3.18.
[23] The actual implementations of the MAC address randomization technique vary largely in different devices.
[24] Moreover, various flaws and shortcomings in these implementations may allow an attacker to track a device even if its MAC address is changed, for instance its probe requests' other elements,[25][26] or their timing.
[29] Using wireless access points in SSID-hidden mode (network cloaking), a mobile wireless device may not only disclose its own MAC address when traveling, but even the MAC addresses associated to SSIDs the device has already connected to, if they are configured to send these as part of probe request packets.
[30] The standard (IEEE 802) format for printing EUI-48 addresses in human-friendly form is six groups of two hexadecimal digits, separated by hyphens (-) in transmission order (e.g. 01-23-45-67-89-AB).
[31] The standard notation, also called canonical format, for MAC addresses is written in transmission order with the least significant bit of each byte transmitted first, and is used in the output of the ifconfig, ip address, and ipconfig commands, for example.