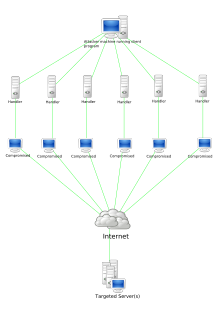
Botnet
[3][4] Botnets are increasingly rented out by cyber criminals as commodities for a variety of purposes,[5] including as booter/stresser services.
[6] In response to efforts to detect and decapitate IRC botnets, bot herders have begun deploying malware on peer-to-peer networks.
For example, Mega-D features a slightly modified Simple Mail Transfer Protocol (SMTP) implementation for testing spam capability.
Botnets of zombie computers are often used to spread e-mail spam and launch denial-of-service attacks (DDoS).
[11] The process of stealing computing resources as a result of a system being joined to a "botnet" is sometimes referred to as "scrumping".
[12] Global law enforcement agencies, with the DOJ and FBI, dismantled the 911 S5 botnet, responsible for $5.9 billion in theft and various cybercrimes.
Chinese national YunHe Wang, charged with operating the botnet, faces up to 65 years in prison.
[13] Botnet command and control (C&C) protocols have been implemented in a number of ways, from traditional IRC approaches to more sophisticated versions.
IRC networks use simple, low bandwidth communication methods, making them widely used to host botnets.
They tend to be relatively simple in construction and have been used with moderate success for coordinating DDoS attacks and spam campaigns while being able to continually switch channels to avoid being taken down.
Anti-malware organizations can detect and shut down these servers and channels, effectively halting the botnet attack.
A botnet adversary can even potentially gain knowledge of the control scheme and imitate the bot herder by issuing commands correctly.
The advantages of using web pages or domains as C&C is that a large botnet can be effectively controlled and maintained with very simple code that can be readily updated.
Disadvantages of using this method are that it uses a considerable amount of bandwidth at large scale, and domains can be quickly seized by government agencies with little effort.
Some botnets use free DNS hosting services such as DynDns.org, No-IP.com, and Afraid.org to point a subdomain towards an IRC server that harbors the bots.
While these free DNS services do not themselves host attacks, they provide reference points (often hard-coded into the botnet executable).
This malware will typically install modules that allow the computer to be commanded and controlled by the botnet's operator.
When the re-connection is made, depending on how it is written, a Trojan may then delete itself or may remain present to update and maintain the modules.
In some cases, a botnet may be temporarily created by volunteer hacktivists, such as with implementations of the Low Orbit Ion Cannon as used by 4chan members during Project Chanology in 2010.
Computer security experts have succeeded in destroying or subverting malware command and control networks, by, among other means, seizing servers or getting them cut off from the Internet, denying access to domains that were due to be used by malware to contact its C&C infrastructure, and, in some cases, breaking into the C&C network itself.
Host-based techniques use heuristics to identify bot behavior that has bypassed conventional anti-virus software.
Researchers at Sandia National Laboratories are analyzing botnets' behavior by simultaneously running one million Linux kernels—a similar scale to a botnet—as virtual machines on a 4,480-node high-performance computer cluster to emulate a very large network, allowing them to watch how botnets work and experiment with ways to stop them.
For example, an automated attack can deploy a large bot army and apply brute-force methods with highly accurate username and password lists to hack into accounts.
On 15 July 2014, the Subcommittee on Crime and Terrorism of the Committee[45] on the Judiciary, United States Senate, held a hearing on the threats posed by botnets and the public and private efforts to disrupt and dismantle them.
It captures network behavior snapshots and employs deep autoencoders to identify abnormal traffic from compromised IoT devices.
This kind of comparison is good because it lets researchers evaluate the methods fairly and find ways to make them better.