Honeypot (computing)
Honeypots can be used for everything from slowing down or stopping automated attacks, capturing new exploits, to gathering intelligence on emerging threats or early warning and prediction.
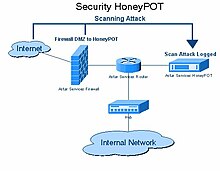
[5] Research honeypots are run to gather information about the motives and tactics of the black hat community targeting different networks.
The activities of the attacker are monitored by using a bug tap that has been installed on the honeypot's link to the network.
In general, high-interaction honeypots provide more security by being difficult to detect, but they are expensive to maintain.
[11] Probably the most famous open proxy was the default configuration of sendmail (before version 8.9.0 in 1998) which would forward email to and from any destination.
Deception technology addresses the automated deployment of honeypot resources over a large commercial enterprise or government institution.
Some system administrators have created honeypot programs that masquerade as these abusable resources to discover spammer activity.
These honeypots can reveal the abuser's IP address and provide bulk spam capture (which enables operators to determine spammers' URLs and response mechanisms).
As described by M. Edwards at ITPRo Today: Typically, spammers test a mail server for open relaying by simply sending themselves an email message.
If the spammer receives the email message, the mail server obviously allows open relaying.
In the early days of anti-spam honeypots, spammers, with little concern for hiding their location, felt safe testing for vulnerabilities and sending spam directly from their own systems.
HoneyPLC is a medium interaction honeypot that can simulate Siemens, Rockwell and other PLC brands.
[32] The second risk of honeypots is that they may attract legitimate users due to a lack of communication in large-scale enterprise networks.
Typically, a honey net is used for monitoring a larger and/or more diverse network in which one honeypot may not be sufficient.
Honey nets and honeypots are usually implemented as parts of larger network intrusion detection systems.
[35] The concept of the honey net first began in 1999 when Lance Spitzner, founder of the Honeynet Project, published the paper "To Build a Honeypot".
On January 7, 1991, while he worked at AT&T Bell Laboratories Cheswick observed a criminal hacker, known as a cracker, attempting to obtain a copy of a password file.
Cheswick wrote that he and colleagues constructed a "chroot "Jail" (or "roach motel")" which allowed them to observe their attacker over a period of several months.
[38] In 2017, Dutch police used honeypot techniques to track down users of the darknet market Hansa.
The metaphor of a bear being attracted to and stealing honey is common in many traditions, including Germanic, Celtic, and Slavic.
The tradition of bears stealing honey has been passed down through stories and folklore, especially the well known Winnie the Pooh.