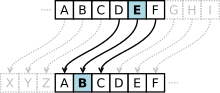
Caesar cipher
[2] Encryption of a letter x by a shift n can be described mathematically as,[3] Decryption is performed similarly, (Here, "mod" refers to the modulo operation.
[8] A piece of text encrypted in a Hebrew version of the Caesar cipher is sometimes found on the back of Jewish mezuzah scrolls.
[9][10] In the 19th century, the personal advertisements section in newspapers would sometimes be used to exchange messages encrypted using simple cipher schemes.
David Kahn (1967) describes instances of lovers engaging in secret communications enciphered using the Caesar cipher in The Times.
[14] If the keyword is as long as the message, is chosen at random, never becomes known to anyone else, and is never reused, this is the one-time pad cipher, proven unbreakable.
Keywords shorter than the message (e.g., "Complete Victory" used by the Confederacy during the American Civil War), introduce a cyclic pattern that might be detected with a statistically advanced version of frequency analysis.
[15] In April 2006, fugitive Mafia boss Bernardo Provenzano was captured in Sicily partly because some of his messages, clumsily written in a variation of the Caesar cipher, were broken.
[16] In 2011, Rajib Karim was convicted in the United Kingdom of "terrorism offences" after using the Caesar cipher to communicate with Bangladeshi Islamic activists discussing plots to blow up British Airways planes or disrupt their IT networks.
Although the parties had access to far better encryption techniques (Karim himself used PGP for data storage on computer disks), they chose to use their own scheme (implemented in Microsoft Excel), rejecting a more sophisticated code program called Mujahideen Secrets "because 'kaffirs', or non-believers, know about it, so it must be less secure".
This can be achieved, for instance, through the utilization of the chi-squared statistic[22] or by minimizing the sum of squared errors between the observed and known language distributions.
[23] The unicity distance for the Caesar cipher is about 2, meaning that on average at least two characters of ciphertext are required to determine the key.