Kernel page-table isolation
[13] The KPTI patches were based on KAISER (short for Kernel Address Isolation to have Side-channels Efficiently Removed),[6] a technique conceived in 2016[14] and published in June 2017 back when Meltdown was not known yet.
[17] Despite prohibiting access to these kernel mappings, it turns out that there are several side-channel attacks in modern processors that can leak the location of this memory, making it possible to work around KASLR.
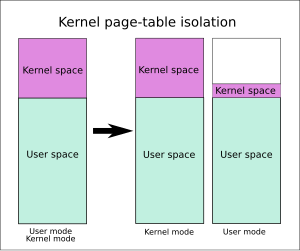
Without KPTI enabled, whenever executing user-space code (applications), Linux would also keep its entire kernel memory mapped in page tables, although protected from access.
One set of page tables includes both kernel-space and user-space addresses same as before, but it is only used when the system is running in kernel mode.
[5] On processors that support the process-context identifiers (PCID), a translation lookaside buffer (TLB) flush can be avoided,[5] but even then it comes at a significant performance cost, particularly in syscall-heavy and interrupt-heavy workloads.
[25] The overhead was measured to be 0.28% according to KAISER's original authors;[6] a Linux developer measured it to be roughly 5% for most workloads and up to 30% in some cases, even with the PCID optimization;[5] for database engine PostgreSQL the impact on read-only tests on an Intel Skylake processor was 7–17% (or 16–23% without PCID),[26] while a full benchmark lost 13–19% (Coffee Lake vs.