Mass surveillance in the United States
The formation and growth of federal law-enforcement and intelligence agencies such as the FBI, CIA, and NSA institutionalized surveillance used to also silence political dissent, as evidenced by COINTELPRO projects which targeted various organizations and individuals.
During the Civil Rights Movement era, many individuals put under surveillance orders were first labelled as integrationists, then deemed subversive, and sometimes suspected to be supportive of the communist model of the United States' rival at the time, the Soviet Union.
[23][24] Regarded as one of the biggest media leaks in the United States, it presented extensive details about the surveillance programs of the NSA, that involved interception of Internet data and telephonic calls from over a billion users, across various countries.
FBI is also directly connected to the bombings, assassinations, and deaths of other people including Malcolm X in 1963, Viola Liuzzo in 1965, Dr. Martin Luther King Jr. in 1968, Anna Mae Pictou Aquash in 1976, and Judi Bari in 1990.
As a result of his political views, Einstein was subjected to telephone tapping, and his mail was searched by the U.S. Federal Bureau of Investigation (FBI) as part of a secret government campaign that aimed to link him with a Soviet espionage ring in order to first discredit him, and then deport him (unsuccessfully) from the United States.
[60] The European Parliament stated in its report that the term "ECHELON" occurred in a number of contexts, but that the evidence presented indicated it was a signals-intelligence collection system capable of interception and content-inspection of telephone calls, fax, e-mail and other data-traffic globally.
[62][63] We will come together to strengthen our intelligence capabilities to know the plans of terrorists before they act and to find them before they strike.In the aftermath of the September 2001 attacks on the World Trade Center and the Pentagon, bulk domestic spying in the United States increased dramatically.
"[72] The article cites anonymous sources that described the program's reach on American citizens: ... it means that the government has detailed records of calls they made — across town or across the country — to family members, co-workers, business contacts and others.
[73] On 15 March 2012, the American magazine Wired published an article with the headline "The NSA Is Building the Country's Biggest Spy Center (Watch What You Say)",[74] which was later mentioned by U.S. Rep. Hank Johnson during a congressional hearing.
In response to Johnson's inquiry, NSA director Keith B. Alexander testified that these allegations made by Wired magazine were untrue: Under construction by contractors with top-secret clearances, the blandly named Utah Data Center is being built for the National Security Agency.
Its purpose: to intercept, decipher, analyze, and store vast swaths of the world's communications as they zap down from satellites and zip through the underground and undersea cables of international, foreign, and domestic networks.
Flowing through its servers and routers and stored in near-bottomless databases will be all forms of communication, including the complete contents of private emails, cell phone calls, and Google searches, as well as all sorts of personal data trails—parking receipts, travel itineraries, bookstore purchases, and other digital "pocket litter."
It is, in some measure, the realization of the "total information awareness" program created during the first term of the Bush administration—an effort that was killed by Congress in 2003 after it caused an outcry over its potential for invading Americans' privacy.
And code-breaking is crucial, because much of the data that the center will handle—financial information, stock transactions, business deals, foreign military and diplomatic secrets, legal documents, confidential personal communications—will be heavily encrypted ...[74] Representative Johnson: "The author of the Wired magazine article, his name is James Bashford, [sic] he writes that NSA has software that "searches U.S. sources for target addresses, locations, countries and phone numbers as well as watchlisted names, keywords, and phrases in email.
"[75] On 6 June 2013, Britain's The Guardian newspaper began publishing a series of revelations by an unnamed American whistleblower, revealed several days later to be former CIA and NSA-contracted systems analyst Edward Snowden.
[25] In over two months of publications, it became clear that the NSA operates a complex web of spying programs which allow it to intercept internet and telephone conversations from over a billion users from dozens of countries around the world.
In addition to this, many of the NSA's programs are directly aided by national and foreign intelligence services, Britain's GCHQ and Australia's DSD, as well as by large private telecommunications and Internet corporations, such as Verizon, Telstra,[79] Google and Facebook.
[80] On 9 June 2013, Edward Snowden told The Guardian: They (the NSA) can use the system to go back in time and scrutinize every decision you've ever made, every friend you've ever discussed something with, and attack you on that basis to sort of derive suspicion from an innocent life and paint anyone in the context of a wrongdoer.The US government has aggressively sought to dismiss and challenge Fourth Amendment cases raised: Hepting v. AT&T, Jewel v. NSA, Clapper v. Amnesty International, Al-Haramain Islamic Foundation v. Obama, and Center for Constitutional Rights v. Bush.
[91] "The Fourth Amendment typically requires 'a neutral and detached authority be interposed between the police and the public,' and it is offended by 'general warrants' and laws that allow searches to be conducted 'indiscriminately and without regard to their connections with a crime under investigation,'" he wrote.
[92] He added: I cannot imagine a more 'indiscriminate' and 'arbitrary invasion' than this systematic and high-tech collection and retention of personal data on virtually every single citizen for purposes of querying and analyzing it without prior judicial approval.
[92]Leon granted the request for a preliminary injunction that blocks the collection of phone data for two private plaintiffs (Larry Klayman, a conservative lawyer, and Charles Strange, father of a cryptologist killed in Afghanistan when his helicopter was shot down in 2011)[91] and ordered the government to destroy any of their records that have been gathered.
But the judge stayed action on his ruling pending a government appeal, recognizing in his 68-page opinion the "significant national security interests at stake in this case and the novelty of the constitutional issues.
The Communications Assistance for Law Enforcement Act (CALEA), passed in 1994, requires that all U.S. telecommunications companies modify their equipment to allow easy wiretapping of telephone, VoIP, and broadband Internet traffic.
In the second model, "which is closer to what Europe adopted", telephone numbers dialed, contents of Web pages visited, and recipients of e-mail messages must be retained by the ISP for an unspecified amount of time.
Since the September 11 attacks, a vast domestic intelligence apparatus has been built to collect information using FBI, local police, state homeland security offices and military criminal investigators.
According to The Register, the FISA Amendments Act of 2008 "specifically authorizes intelligence agencies to monitor the phone, email, and other communications of U.S. citizens for up to a week without obtaining a warrant" [citation needed] when one of the parties is outside the U.S. PRISM was first publicly revealed on 6 June 2013, after classified documents about the program were leaked to The Washington Post and The Guardian by Edward Snowden.
[144] These cameras also work as transit choke-points that allow individuals inside the vehicle to be positively identified and license plate data to be collected and time stamped for cross reference with airborne WAMI such as ARGUS and HAWKEYE used by police and Law Enforcement.
[148] The report claims that the SFPD's usage of the camera network went beyond investigating footage, likening the department's access to real-time video feeds as "indiscriminate surveillance of protestors.
"[148] On 19 June 2013, FBI Director Robert Mueller told the United States Senate Committee on the Judiciary that the federal government had been employing surveillance drones on U.S. soil in "particular incidents".
[179] In a statement addressed to the National Congress of Brazil, journalist Glenn Greenwald testified that the U.S. government uses counter-terrorism as a "pretext" for clandestine surveillance in order to compete with other countries in the "business, industrial and economic fields".



See also : Hollywood blacklist



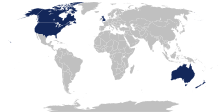

Left : SEA-ME-WE 3 , which runs across the Afro-Eurasian supercontinent from Japan to Northern Germany , is one of the most important submarine cables accessed by the "Five Eyes". Singapore, a former British colony in the Asia-Pacific region (blue dot), plays a vital role in intercepting Internet and telecommunications traffic heading from Australia/Japan to Europe, and vice versa. An intelligence sharing agreement between Singapore and Australia allows the rest of the "Five Eyes" to gain access to SEA-ME-WE 3 . [ 167 ]
Right : TAT-14 , a telecommunications cable linking Europe with the United States, was identified as one of few assets of "Critical Infrastructure and Key Resources" of the USA on foreign territory. In 2013, it was revealed that British officials "pressured a handful of telecommunications and internet companies" to allow the British government to gain access to TAT-14 . [ 170 ]