Network Time Protocol
NTP is intended to synchronize participating computers to within a few milliseconds of Coordinated Universal Time (UTC).
[2][3] The protocol is usually described in terms of a client–server model, but can as easily be used in peer-to-peer relationships where both peers consider the other to be a potential time source.
[4][5]: 16 They can also use broadcasting or multicasting, where clients passively listen to time updates after an initial round-trip calibrating exchange.
The technology was later described in the 1981 Internet Engineering Note (IEN) 173[18] and a public protocol was developed from it that was documented in RFC 778.
More complete synchronization systems, although lacking NTP's data analysis and clock disciplining algorithms, include the Unix daemon timed, which uses an election algorithm to appoint a server for all the clients;[19] and the Digital Time Synchronization Service (DTSS), which uses a hierarchy of servers similar to the NTP stratum model.
It drew on the experimental results and clock filter algorithm documented in RFC 956 and was the first version to describe the client–server and peer-to-peer modes.
In 1991, the NTPv1 architecture, protocol and algorithms were brought to the attention of a wider engineering community with the publication of an article by David L. Mills in the IEEE Transactions on Communications.
However the design of NTPv2 was criticized for lacking formal correctness by the DTSS community, and the clock selection procedure was modified to incorporate Marzullo's algorithm for NTPv3 onwards.
The RFC included an analysis of all sources of error, from the reference clock down to the final client, which enabled the calculation of a metric that helps choose the best server where several candidates appear to disagree.
In subsequent years, as new features were added and algorithm improvements were made, it became apparent that a new protocol version was required.
[23] Following the retirement of Mills from the University of Delaware, the reference implementation is currently maintained as an open source project led by Harlan Stenn.
[24][25] On the IANA side, a ntp (network time protocols) work group is in charge of reviewing proposed drafts.
[23] An unrelated draft termed "NTPv5" by M. Lichvar of chrony was initiated in 2020 and includes security, accuracy, and scaling changes.
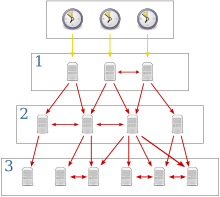
The NTP algorithms on each computer interact to construct a Bellman–Ford shortest-path spanning tree, to minimize the accumulated round-trip delay to the stratum 1 servers for all the clients.
[5] The refid field is filled with status words in the case of kiss-o'-death (KoD) packets, which tell the client to stop sending requests so that the server can rest.
[37] According to Mills, "The 64-bit value for the fraction is enough to resolve the amount of time it takes a photon to pass an electron at the speed of light.
[1]: 20 Accurate synchronization is achieved when both the incoming and outgoing routes between the client and the server have symmetrical nominal delay.
If the routes do not have a common nominal delay, a systematic bias exists of half the difference between the forward and backward travel times.
W32Time was originally implemented for the purpose of the Kerberos version 5 authentication protocol, which required time to be within 5 minutes of the correct value to prevent replay attacks.
[46] If higher accuracy is desired, Microsoft recommends using a newer version of Windows or different NTP implementation.
[48][46][49] In 2004, Henning Brauer of OpenBSD presented OpenNTPD, an NTPv3/SNTPv4[50] implementation with a focus on security and encompassing a privilege separated design.
Whilst it is aimed more closely at the simpler generic needs of OpenBSD users, it also includes some protocol security improvements while still being compatible with existing NTP servers.
[55] chrony is an independent NTP implementation mainly sponsored by Red Hat, who uses it as the default time program in their distributions.
[61] chrony is available under GNU General Public License version 2, was created by Richard Curnow in 1997 and is currently maintained by Miroslav Lichvar.
[63] ntpd-rs is part of the "Pendulum" project which also includes a Precision Time Protocol implementation "statime".
On the day of a leap second event, ntpd receives notification from either a configuration file, an attached reference clock, or a remote server.
Some other implementations, such as OpenNTPD, have smaller code base and adopted other mitigation measures like privilege separation, are not subject to this flaw.
The public key system known as "autokey" in NTPv4 adapted from IPSec offers useful authentication,[82] but is not practical for a busy server.
[83] Autokey was also later found to suffer from several design flaws,[90] with no correction published, save for a change in the message authentication code.
[92] The main improvement over previous attempts is that a separate "key establishment" server handles the heavy asymmetric cryptography, which needs to be done only once.




ntpq
under
Windows 11
being used to query the state of stratum 1 time servers and verify proper operation of the client.

