Attack tree
They are widely used in the fields of defense and aerospace for the analysis of threats against tamper resistant electronics systems (e.g., avionics on military aircraft).
[2] Attack trees are increasingly being applied to computer control systems (especially relating to the electric power grid).
Some of the earliest descriptions of attack trees are found in papers and articles by Bruce Schneier,[4] when he was CTO of Counterpane Internet Security.
However, the attributions in some of the early publicly available papers on attack trees[5] also suggest the involvement of the National Security Agency in the initial development.
Threat trees were developed by Jonathan Weiss of Bell Laboratories to comply with guidance in MIL STD 1785[6] for AT&T's work on Command and Control for federal applications, and were first described in his paper in 1982.
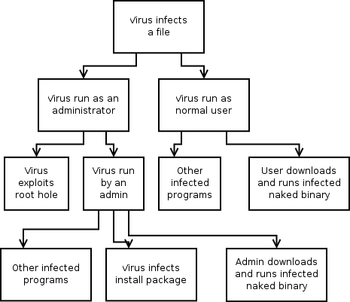
Thus a four level attack tree can be drawn, of which one path is (Bribe Keyholder, Obtain Key, Unlock Lock, Steal Computer).
This adds to the attack tree the possibility of design flaws or exploits in the package manager.
Although this is theoretically sound, it is not usually possible to simply mitigate a threat without other implications to the continued operation of the system.
Implementing this negates any way, foreseen or unforeseen, that a normal user may come to infect the operating system with a virus[citation needed]; however, it also requires that users switch to an administrative account to carry out administrative tasks, thus creating a different set of threats on the tree and more operational overhead.
Systems using cooperative agents that dynamically examine and identify vulnerability chains, creating attack trees, have been built since 2000.