Cipher
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure.
Codes operated by substituting according to a large codebook which linked a random string of characters or numbers to a word or phrase.
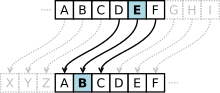
The operation of a cipher usually depends on a piece of auxiliary information, called a key (or, in traditional NSA parlance, a cryptovariable).
The encrypting procedure is varied depending on the key, which changes the detailed operation of the algorithm.
Without knowledge of the key, it should be extremely difficult, if not impossible, to decrypt the resulting ciphertext into readable plaintext.
In casual contexts, "code" and "cipher" can typically be used interchangeably; however, the technical usages of the words refer to different concepts.
Codes contain meaning; words and phrases are assigned to numbers or symbols, creating a shorter message.
However, codes have a variety of drawbacks, including susceptibility to cryptanalysis and the difficulty of managing a cumbersome codebook.
[2][3] In the 1640s, the Parliamentarian commander, Edward Montagu, 2nd Earl of Manchester, developed ciphers to send coded messages to his allies during the English Civil War.
[5] It is possible to create a secure pen and paper cipher based on a one-time pad, but these have other disadvantages.
[12] Ciphers can be distinguished into two types by the type of input data: In a pure mathematical attack, (i.e., lacking any other information to help break a cipher) two factors above all count: Since the desired effect is computational difficulty, in theory one would choose an algorithm and desired difficulty level, thus decide the key length accordingly.
Claude Shannon proved, using information theory considerations, that any theoretically unbreakable cipher must have keys which are at least as long as the plaintext, and used only once: one-time pad.