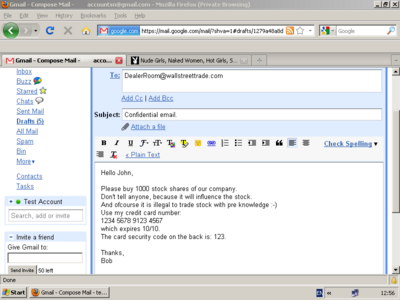
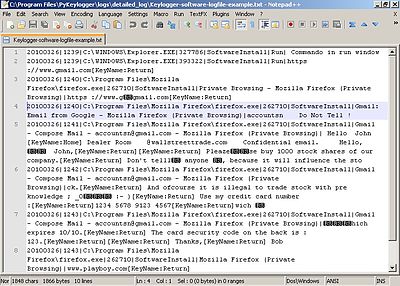
Keystroke logging
[4][5] Keystroke logging can also be utilized to monitor activities of children in schools or at home and by law enforcement officials to investigate malicious usage.
The user-mode program operated by locating and dumping character lists (clients) as they were assembled in the Unix kernel.
Microsoft publicly stated that Windows 10 has a built-in keylogger in its final version "to improve typing and writing services".
From a technical perspective, there are several categories: Since 2006, keystroke logging has been an established research method for the study of writing processes.
[21][22] Different programs have been developed to collect online process data of writing activities,[23] including Inputlog, Scriptlog, Translog and GGXLog.
Software keyloggers may be augmented with features that capture user information without relying on keyboard key presses as the sole input.
Some of these features include: Hardware-based keyloggers do not depend upon any software being installed as they exist at a hardware level in a computer system.
Writing simple software applications for keylogging can be trivial, and like any nefarious computer program, can be distributed as a trojan horse or as part of a virus.
What is not trivial for an attacker, however, is installing a covert keystroke logger without getting caught and downloading data that has been logged without being traced.
They presented a deniable password snatching attack in which the keystroke logging trojan is installed using a virus or worm.
The cryptotrojan asymmetrically encrypts the pilfered login/password pairs using the public key of the trojan author and covertly broadcasts the resulting ciphertext.
[46] Also in 2000, the FBI lured two suspected Russian cybercriminals to the US in an elaborate ruse, and captured their usernames and passwords with a keylogger that was covertly installed on a machine that they used to access their computers in Russia.
Automatic form-filling programs may prevent keylogging by removing the requirement for a user to type personal details and passwords using the keyboard.
Form fillers are primarily designed for Web browsers to fill in checkout pages and log users into their accounts.
However, someone with physical access to the machine may still be able to install software that can intercept this information elsewhere in the operating system or while in transit on the network.
(Transport Layer Security (TLS) reduces the risk that data in transit may be intercepted by network sniffers and proxy tools.)
However, an attacker who has remote control over such a computer can simply wait for the victim to enter their credentials before performing unauthorized transactions on their behalf while their session is active.
Similar to on-screen keyboards, speech-to-text conversion software can also be used against keyloggers, since there are no typing or mouse movements involved.
Many PDAs and lately tablet PCs can already convert pen (also called stylus) movements on their touchscreens to computer understandable text successfully.
Lastly, someone can also use context menus to remove, cut, copy, and paste parts of the typed text without using the keyboard.