Steganography tools
Certain properties can raise suspicion that a file is carrying hidden data: It is a cryptographic requirement that the carrier (e.g. photo) is original, not a copy of something publicly available (e.g., downloaded).
The sheer volume of modern (ca 2014) and inane high-bandwidth media (e.g., youtube.com, bittorrent sources.
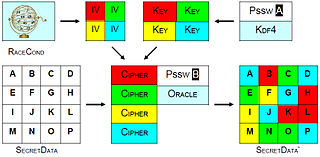
This additional security feature usually is achieved by: Steganography tools aim to ensure robustness against modern forensic methods, such as statistical steganalysis.
Strong steganography software relies on a multi-layered architecture with a deep, documented obfuscation process.
Different file formats are modified in different ways, in order to covertly insert hidden data inside them.