Defense in depth (computing)
The idea behind the defense in depth approach is to defend a system against any particular attack using several independent methods.
[3][4] The term defense in depth in computing is inspired by a military strategy of the same name, but is quite different in concept.
The military strategy revolves around having a weaker perimeter defense and intentionally yielding space to buy time, envelop, and ultimately counter-attack an opponent, whereas the information security strategy simply involves multiple layers of controls, but not intentionally ceding ground (cf.
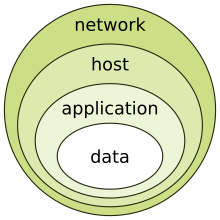
[10] With this approach, defense in depth can be conceptualized as three distinct layers or planes laid one on top of the other.
[12] Both perspectives are equally valid, and each provides valuable insight into the implementation of a good defense in depth strategy.