Firewall (computing)
The term firewall originally referred to a wall intended to confine a fire within a line of adjacent buildings.
[7] Before it was used in real-life computing, the term appeared in John Badham's 1983 computer‑hacking movie WarGames, spoken by the bearded and bespectacled programmer named Paul Richter, which possibly inspired its later use.
The innovative PIX solution quickly gained industry acclaim, earning the prestigious "Hot Product of the Year" award from Data Communications Magazine in January 1995.
The PIX became one of Cisco's flagship firewall product lines before eventually being succeeded by the Adaptive Security Appliance (ASA) platform introduced in 2005.
The bulk of Internet communication in 20th and early 21st century used either Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) in conjunction with well-known ports, enabling firewalls of that era to distinguish between specific types of traffic such as web browsing, remote printing, email transmission, and file transfers.
At AT&T Bell Labs, Bill Cheswick and Steve Bellovin continued their research in packet filtering and developed a working model for their own company based on their original first-generation architecture.
[19] In 1992, Steven McCanne and Van Jacobson released a paper on BSD Packet Filter (BPF) while at Lawrence Berkeley Laboratory.
[20][21] From 1989–1990, three colleagues from AT&T Bell Laboratories, Dave Presotto, Janardan Sharma, and Kshitij Nigam, developed the second generation of firewalls, calling them circuit-level gateways.
[27] It can also provide unified security management including enforced encrypted DNS and virtual private networking.
These policies, collectively known as firewall rules, are the specific guidelines that determine the traffic allowed or blocked across a network's boundaries.
These attributes commonly include: Zones are logical segments within a network that group together devices with similar security requirements.
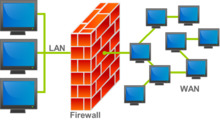
By partitioning a network into zones, such as "Technical", "WAN", "LAN", "Public," "Private," "DMZ", and "Wireless," administrators can enforce policies that control the flow of traffic between them.
Each zone has its own level of trust and is governed by specific firewall rules that regulate the ingress and egress of data.
Implementing firewall rules based on IP addresses alone is often insufficient due to the dynamic nature of user location and device usage.
With this setup, only users who authenticate and are identified as members of "Students" are denied to access social media servers.